ShadowPlex Products
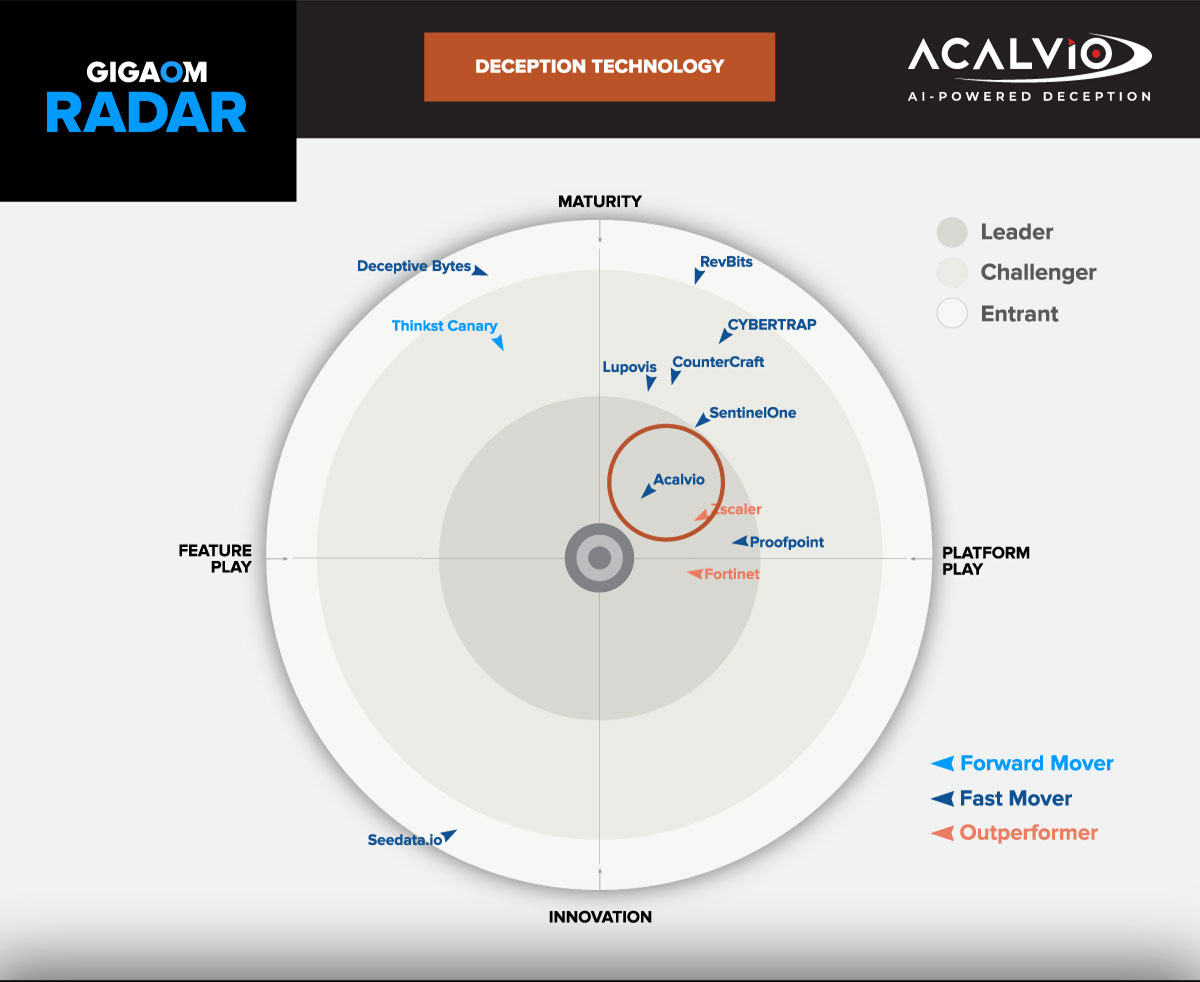
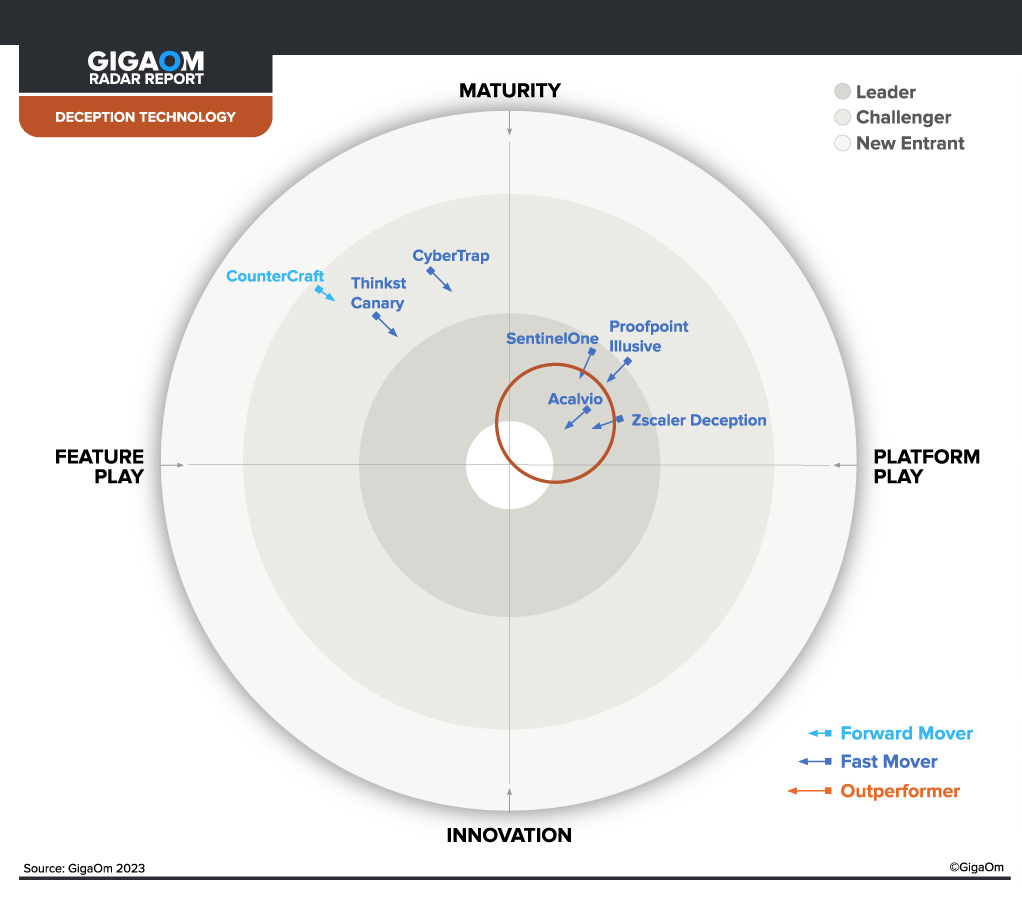
Acalvio is the leader in Cyber Deception technology, built on over 25 issued patents in Autonomous Deception and advanced AI. The Acalvio Active Defense Platform provides robust Identity Protection, Advanced Threat Defense, and Threat Hunting products.
Acalvio Active Defense Platform
Built on Award-winning and Patented Cyber Deception Technology
Identity Protection
Provides unprecedented visibility to the identity attack surface and deception-based Identity Threat Detection and Response (ITDR)
Advanced Threat Defense
Combines breakthrough Deception Technology with Advanced AI for early detection of cyber threats with precision and speed
Honeytokens for CrowdStrike
a wide variety of identity threats with precision and speed.
What is Deception-based Active Defense?
Why do I need Acalvio Active Defense?
Deception Technology Flips the
Advantage Back to Defense
In this 1-minute video, former Vice Chairman of the Joint Chiefs of Staff Admiral James “Sandy” Winnefeld discusses the value of deception technology. A determined adversary is eventually going to get through to your network. Deception Technology flips the advantage back to the defense.
Active Defense Against Cyber
Threats with Acalvio
In this 2-minute video, Ram Varadarajan, Co-Founder and CEO of Acalvio Technologies, provides an overview of Acalvio Active Defense Platform built with the innovations in Cyber Deception technologies and discusses how it helps enterprises actively defend against advanced security threats.
Latest Highlights
Next Steps
Explore our patented technologies to enable Active Defense and Identity Protection in your enterprise.