Acalvio Honey Accounts and Honeytokens for CrowdStrike Falcon® Identity Protection
Introduction
Identity threats are involved in 80 percent of all cyberattacks. They are serious threats that compromise corporate and personal information. Sophisticated attackers like APTs and ransomware actors typically start a campaign with an attack on identities. Attackers can exploit identities on endpoints, applications, and even identity stores.
An identity attack is hard to detect with traditional cybersecurity approaches.
Acalvio ShadowPlex honey accounts and honey tokens are a new layer in the Defense-in-Depth offering for Identity Protection. They are the perfect complement to traditional approaches for securing identities in the enterprise network.
Honeytoken Accounts and HoneyTokens
Honeytoken accounts and honeytokens embody Deception Technology techniques. Honeytoken accounts are deceptive user accounts, service accounts, and application identities created in Active Directory (AD). They are specifically designed to lure attackers. Honeytokens are deceptive credentials and data that are embedded in legitimate assets such as Falcon-managed endpoints and cloud workloads. Together, they are very effective at detecting identity threats.

Figure1: ShadowPlex recommended Honeytoken Accounts in Falcon® Identity Protection console
CrowdStrike Falcon® Identity Protection has built-in support for monitoring honey accounts and a policy-based identity threat containment and response mechanism. Any access or alterations of honey accounts trigger a dedicated high-fidelity detection, giving SOC analysts visibility into the adversary attack path.
Automated Deployment and Maintenance
If security administrators were to manually create honey accounts in AD, it would be an involved and challenging process, given the various design dimensions to consider in making honey accounts effective and attractive to attackers. Acalvio ShadowPlex abstracts away these challenges by bringing in years of domain expertise in Deception Technology. Acalvio’s platform is seamlessly pre-integrated with the CrowdStrike Falcon® platform to enable CrowdStrike customers to leverage the power of honey accounts and honeytokens easily and quickly.
Honeytokens created by the Acalvio ShadowPlex platform blend well with existing identity caches on endpoints. Honeytokens extend the power of honey accounts to Falcon-managed endpoints and even unmanaged endpoints.
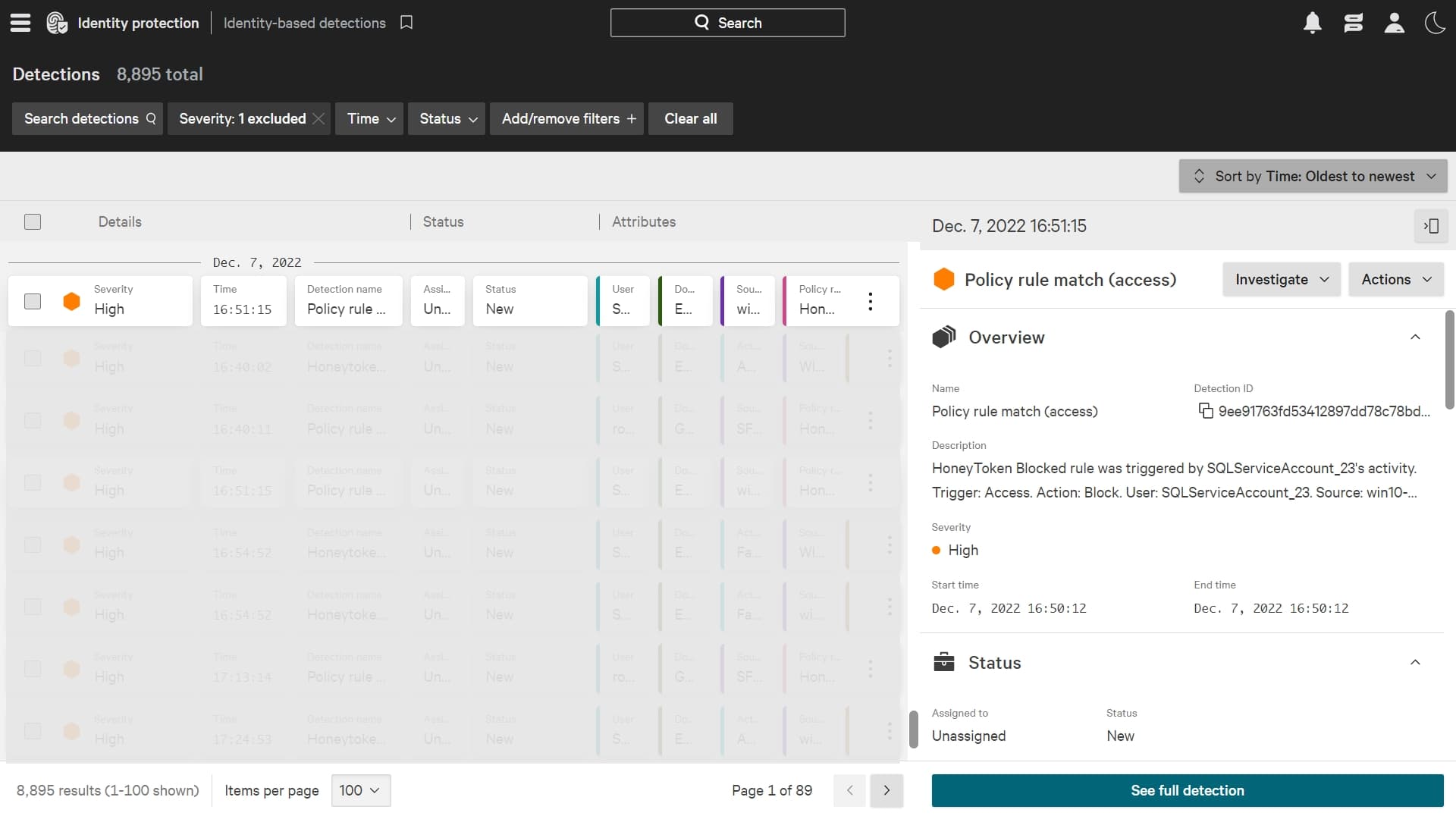
Figure2: Honeytoken activity blocked using policy settings
The Honeytokens fulfillment capability from Acalvio is a completely automated solution, pre-integrated into the Falcon® platform, and does not require any additional Acalvio software to be installed. Acalvio provides a single console solution to CrowdStrike Falcon® customers.
Benefits
The Acalvio ShadowPlex offers the following benefits with the use of honey accounts and honeytokens:
- Fully automated, robust platform to operationalize honey accounts and honeytokens for Identity Protection
- Honeytokens capability is seamlessly extended to Falcon-managed endpoints. This capability includes deployment and refresh lifecycles.
- Advanced AI-based recommendation engine for honey accounts
- Pre-integration with CrowdStrike Falcon® Identity Protection. No additional software to install on enterprise networks.
- Complete control of types and counts of honey accounts being created for customers
- Powerful capability to detect identity threats from managed and unmanaged endpoints, including endpoints in a Zero Trust environment
- SaaS Service for continuous value with no components to install on the enterprise network
Next Steps
Explore our patented technologies to enable Active Defense and Identity Security in your enterprise.