Acalvio ShadowPlex Active Directory Protection
Attacks against AD can have far-reaching consequences for every organization across multiple industries. While the security posture and strategy have taken the main stage at every organization today, the solutions mostly involve increasing audit logging, disabling tools, vulnerability scanning, or installing security agents on endpoints and other assets. While these solutions are necessary, they can only provide a limited solution for advanced threat defense against key assets such as Active Directory.
Acalvio ShadowPlex is an autonomous deception platform that provides an AI-based deception solution for Active Directory protection. ShadowPlex’s strong capabilities include preventing attacks on Active Directory by providing continuous visibility into possible attack surfaces, predicting the attacker’s path, slowing down, confusing or diverting the attacker, predicting and detecting the TTP at every stage, and ultimately, even selectively changing the attacker’s perception of the network.
ShadowPlex supports on-premises AD deployments, Azure AD, and Hybrid AD deployments.
The following are the key features of ShadowPlex’s AD protection solution:
Active Directory InSightsTM
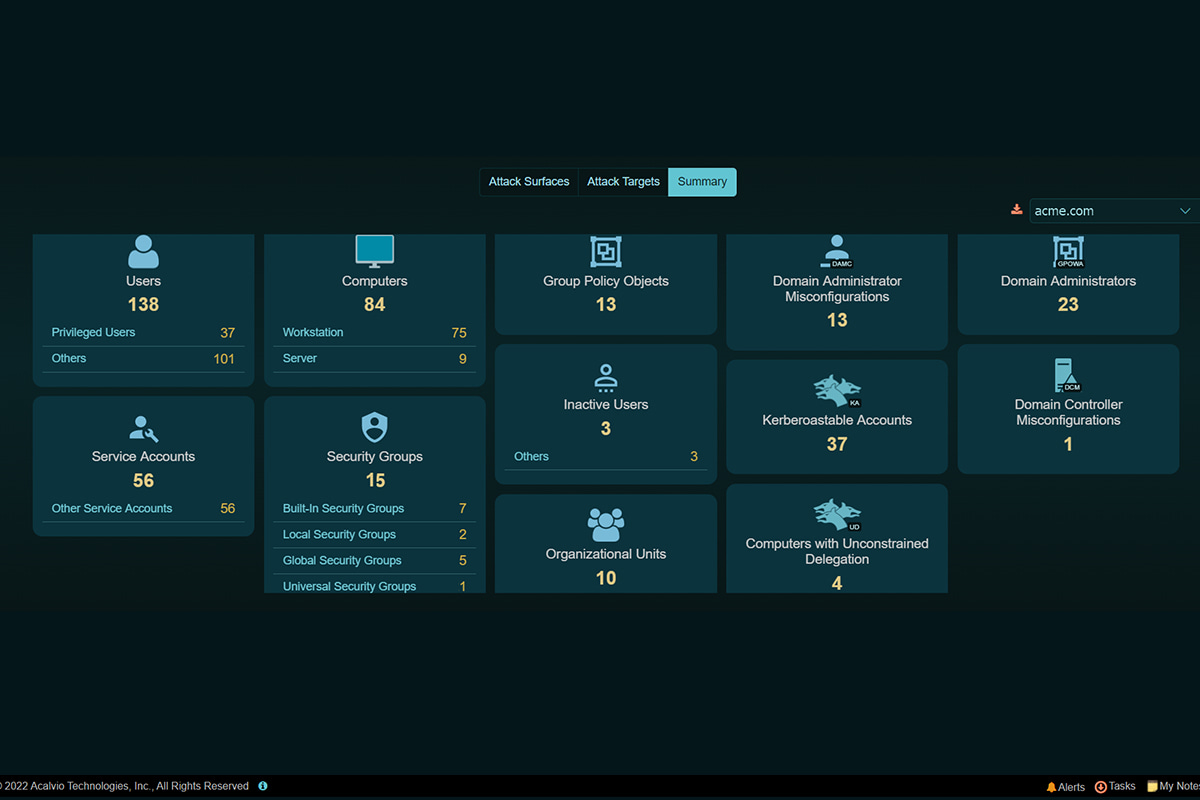
ShadowPlex Active Directory InSightsTM presents an Attacker’s View of the network and reveals the attack surface and risk exposure in the production domains.
The first step in reducing the attacker’s chance for success is to reduce the attack surface. ShadowPlex leverages threat intelligence from various sources using pre-built integrations to build the attacker’s view. This view can be invaluable for the defense teams to proactively reduce the attack surface.
The ShadowPlex AD InSightsTM provides security and IT administrators, continuous visibility into potential security risk exposure introduced by factors such as unprotected administrator accounts, shadow administrators, over-permissioned accounts, kerberoastable accounts, unmanaged SPNs, and service accounts, among other misconfigurations. ShadowPlex generates these extensive insights spanning user and computer accounts, groups, GPOs, ACLs, domains, forests and trust relationships, and other AD artifacts.
Even in modestly complex Active Directory environments, it can often be a challenge to track objects and present the attack surface. ShadowPlex solves this problem without requiring any manual intervention. ShadowPlex does not require any special privileges or permissions on the domain to generate the attack surface insights.
Attack Path Analysis
In any enterprise, with continuous growth and restructuring, there is a complex and evolving ecosystem of users, computers, groups, GPOs, and other objects. Management blind spots, vulnerabilities, misconfigurations, and inadequate access controls in AD present a significant security risk. Attackers leverage AD misconfigurations and vulnerabilities to identify attack paths that facilitate lateral movement and privilege escalation to compromise valuable assets on the network.
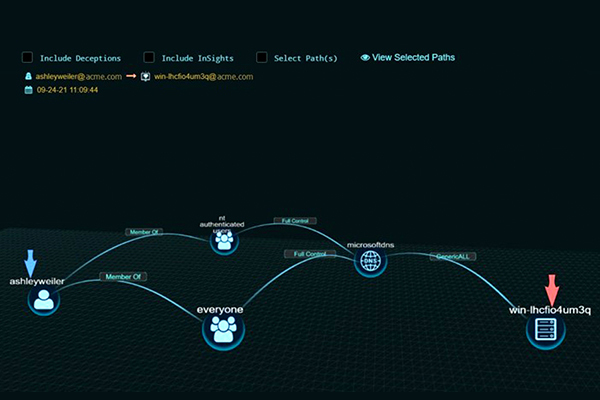
Attackers use tools such as BloodHound to analyze the attack paths on the network and even find the shortest path to their targets. ShadowPlex Attack Path provides the powerful capability for the defense teams to proactively predict these attack paths and remediate them to significantly reduce the exposure.
A typical enterprise may have many viable attack paths that can potentially lead attackers to their targets. ShadowPlex Attack Path combines AI-based Advanced Deception with Graph Theory to identify attack paths involving exploitable chains of relations. Each graph represents potential paths that adversaries can traverse from exploitable accounts or endpoints to reach valuable assets on the network.
This feature serves as a powerful Active Defense tool to proactively disrupt viable attack paths to valuable assets and add deceptions to strengthen defenses.
Curated ShadowPlex Deceptions for Active Directory Protection
Attacks against Active Directory are hard to detect and sometimes even undetectable given that they use legitimate domain credentials, service accounts and domain authenticated computers. Detection using traditional triaging or event log monitoring does not surface conclusive malicious activity.
Acalvio offers an extensive variety of deceptions that is fundamental to Active Directory protection.
ShadowPlex provides pre-defined Active Directory Protection Deceptions that combine targeted deceptions with AI. Deceptions for AD consist of Decoy Computers, Services, User and Service Accounts, and SPNs that are recommended by the AI engine to seamlessly blend into the AD environment. The deceptions are registered in the production AD..
ShadowPlex provides a pre-built curated palette of non-fingerprintable deceptions designed specifically to detect advanced Active Directory attacks, such as:
- KERBEROASTING
- AS-REP ROASTING
- UNCONSTRAINED DELEGATION COMPUTER ATTACKS
- RECON ATTACKS
- DCSYNC
- AZURE AD CONNECT ATTACKS
- ADFS/GOLDEN SAML
Auto Recommendation and Placement of Deceptions
An effective deception strategy should include deceptions that blend into the enterprise environment. In large, complex Active Directory environments, determining the type and placement of deceptions is a practical challenge for enterprises.
ShadowPlex uses AI algorithms to auto-recommend the right type of entity names and attributes such as unique identifiers for SPNs, and best-practice conventions for service accounts among others to make deceptions attractive to attackers. ShadowPlex also devises an effective deception placement strategy to divert attackers away from assets and toward decoys. This capability removes the burden of IT teams manually specifying the properties and placement of deceptions.
Auto recommendation and placement of deceptions is not a one-time activity. Active Directory environments undergo constant change. As a result, deception strategy, deployment, and placement must be reviewed periodically. ShadowPlex runs in autonomous mode, auto-discovers changes, and appropriately adjusts deceptions to blend with the network. It recommends relevant, new deceptions without requiring manual intervention. This is a unique capability aimed at ensuring that deceptions are current and dynamic.
ShadowPlex’s dynamic deceptions combined with AI for blending and recommendation ensure that the deception quality and realism are best-in-class.


Decoy Containment
ShadowPlex has the in-built capability to contain Deceptions (Decoy Computers and Service Accounts/Users) to ensure that attackers cannot use these deceptions to cause harm to the production network. For example, Decoy Computers are contained using the patented ShadowPlex Deception Farms Architecture.
Attackers cannot disable ShadowPlex containment

AI-based Traversal Analysis
ShadowPlex provides a capability for viewing real-time attack progression. ShadowPlex generates the traversal path by leveraging advanced AI techniques. The path shows possible routes that a threat may have taken to reach the asset under investigation.
Automated Response

Solution brief
Acalvio ShadowPlex
Active Directory Protection
Or
Please refer to the articles in our Blog section for more information:

Next Steps
Explore our patented technologies to enable Active Defense and Identity Protection in your enterprise.