Acalvio ShadowPlex Threat Hunting provides a unique set of threat investigation capabilities that leverage cyber deception to improve Security Operations Center (SOC) efficiency. Rapid threat investigation requires narrowing the set of assets that are likely to have been compromised, quick analysis of the collected attack artifacts and automated threat hunting. ShadowPlex Threat Hunting provides capabilities in each of these three areas, besides also providing unified global visibility and situational awareness into attack progression.
ShadowPlex Threat Hunting Capabilities
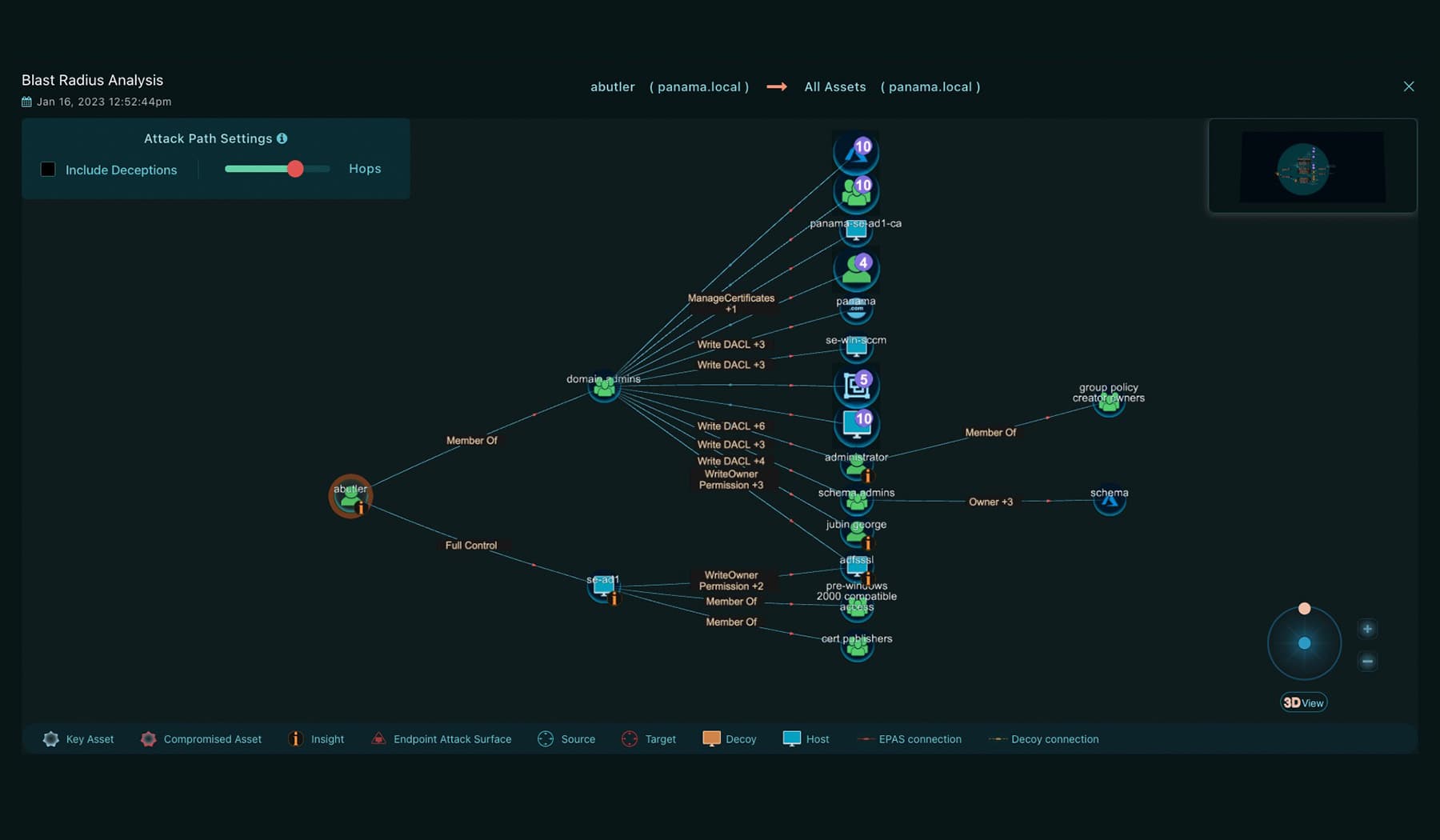
Adversary Traversal
- Uses data from the enterprise data lake to trace the path of the attack through the enterprise network
Active Threat Hunting
- Enables SOC analysts to do hypothesis testing and threat confirmation using deception technology
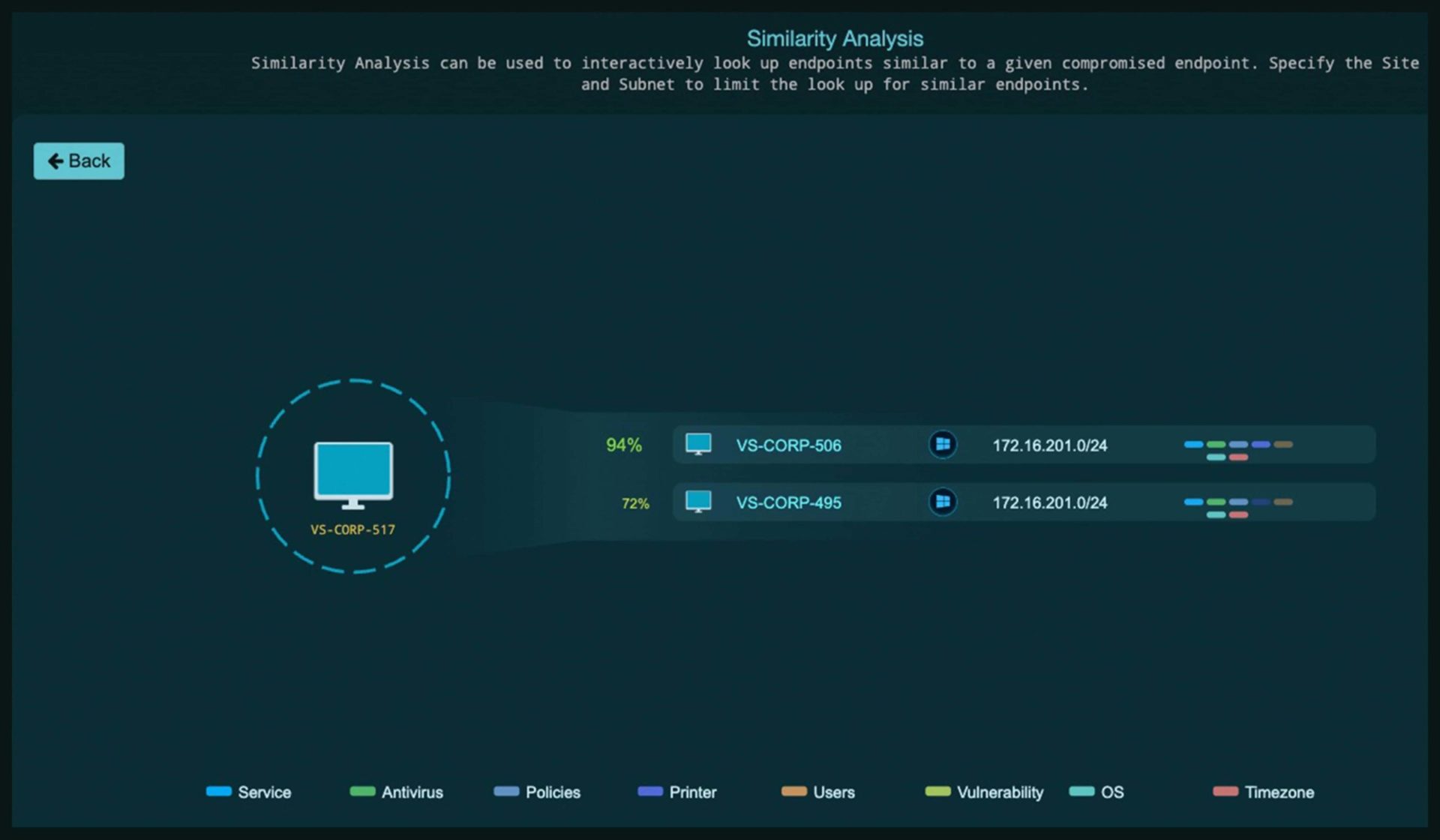
Similarity Analysis
- Leverages data from known compromised machines to determine the list of similar exploitable assets
Link Analysis
- Links events from various security products and highlights relationships across various observations
Targeted Endpoint Forensics
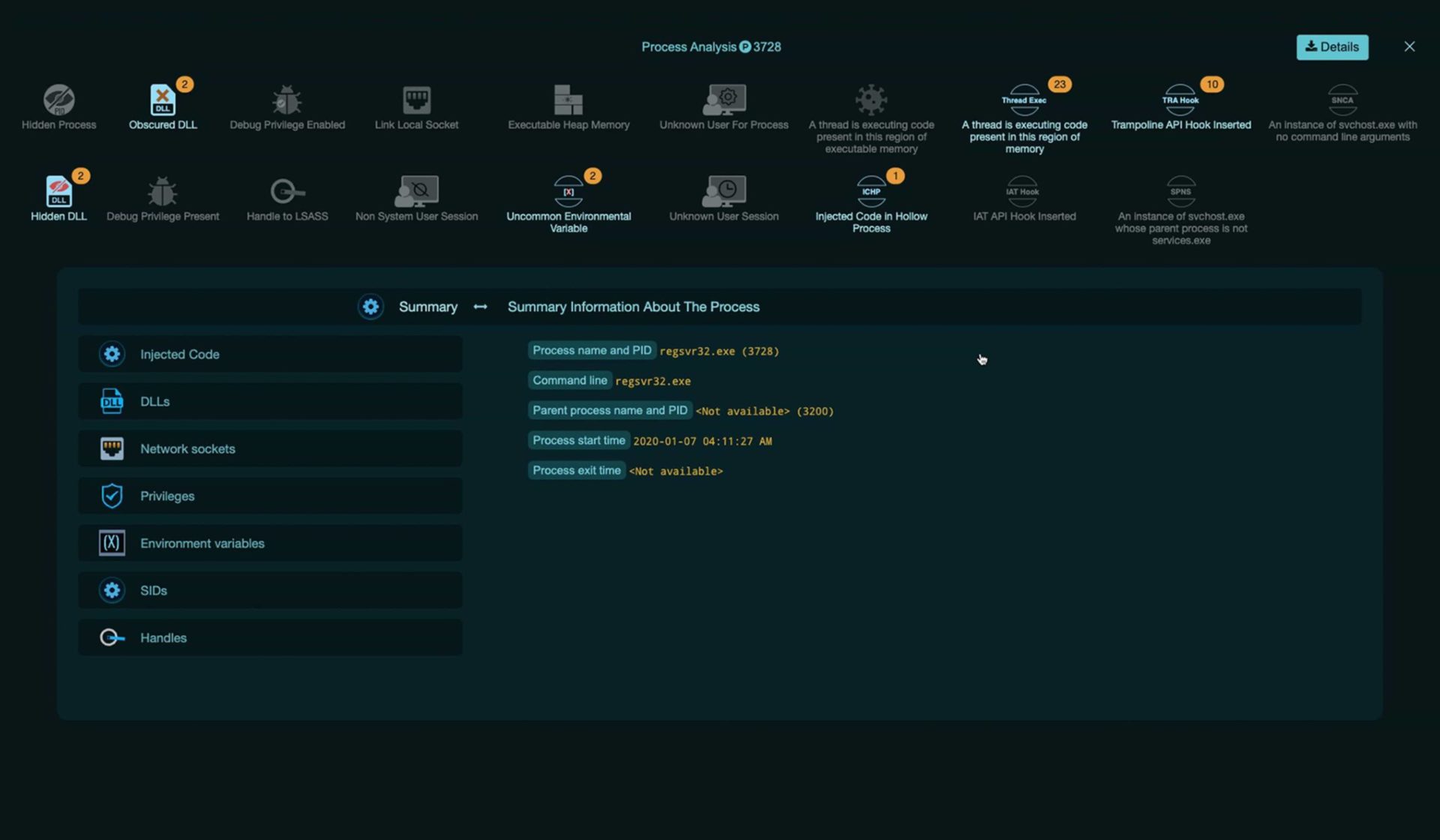
Analysis of Attack Artifacts
- Machine learning based PowerShell script and log analysis, providing capability and attribution
- Memory snapshot analysis for memory-resident malware
Active Threat Hunting

Threat Hunting activities are mandatory to reduce risk and to meet the requirements of recommendations such as the NIST CyberSecurity Framework. The challenge is to execute these activities with limited staff and budget. Advanced Deception solutions are very well suited to meeting this challenge: You simply configure and deploy deception assets such that attackers who satisfy your hunting hypothesis will be attracted to them.
Adversary Traversal

- AI-driven automated analysis leverages a known security incident and uses data from the enterprise data lake to trace the path of the attack through the enterprise network
- Narrows down the set of potential compromised assets and enables rapid investigation
Similarity Analysis

- Innovative AI-driven automated analysis leverages data collected from known compromised machines to determine the list of similar exploitable enterprise assets
- Extracts additional value from existing enterprise data lakes
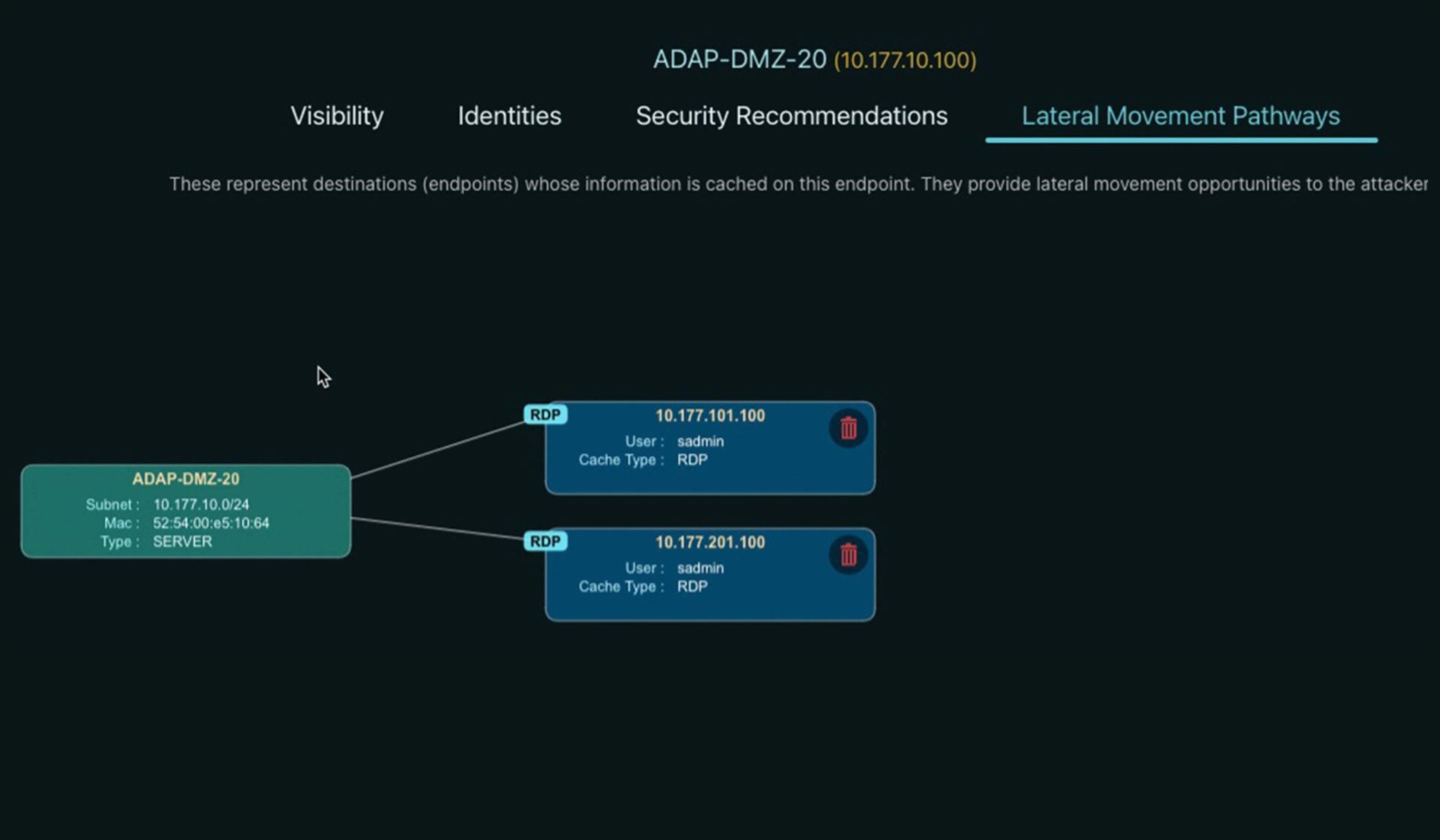
Endpoint Forensics

- Deep and comprehensive forensics collected on any compromised enterprise endpoint
- AI-Driven analysis to determine attack TTPs
- Increases SOC efficiency by making compromised endpoint analysis faster and easier
Many Advanced Analytics

Automated Forensic Evidence Analysis
- PowerShell Logs
- PowerShell Scripts
- Memory dumps
- Event Logs
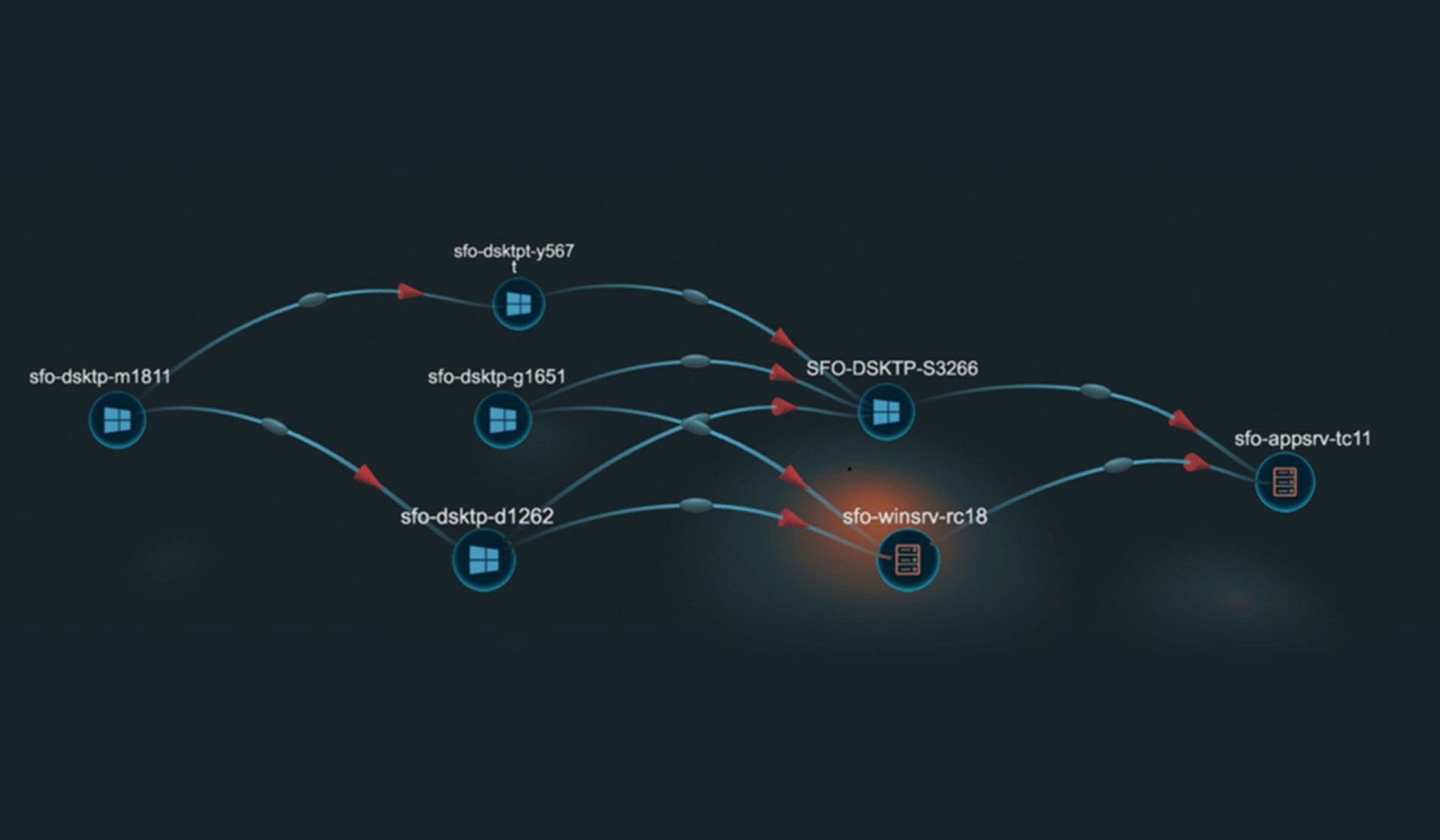
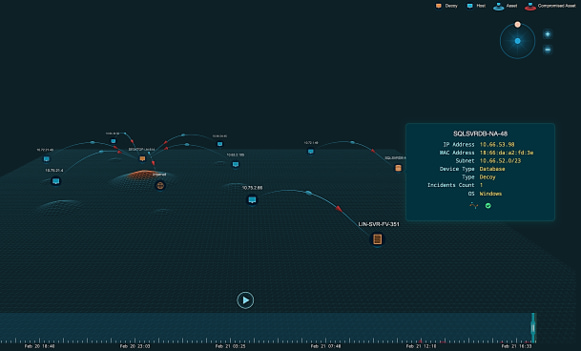
Link Analysis

- Links various security events for holistic view
- Highlights relationships across various observations
- - Deceptions Events
- - Enterprise Endpoints Events
- Shows Attack progression
- Provides context for nodes
- Provides situational awareness
- Shows asset activity heat map
Related Resources
Next Steps
Explore our patented technologies to enable Active Defense and Identity Protection in your enterprise.

