Ransomware models have evolved, with ransomware as a service generating novel ransomware variants to evade detection by traditional security solutions. Ransomware has pivoted to using identity-driven exploits, trusted connection pathways, custom malware variants to evade detection. With ransomware threats adopting double and triple extortion techniques and recovery times taking months, early detection of ransomware is paramount to protect the organization from this threat.
Ransomware Models Have Evolved
Ransomware was traditionally a fully automated, malware centric approach
- Same version across different victim organizations
Ransomware is evolving to adopt APT-style tactics
- Ransomware-as-a Service model
- RaaS is primarily based on human-operated ransomware
Human-operated ransomware is adaptive
- With human decisioning
- Attack sequence is dynamically updated based on what the attacker finds in the environment

Data exfiltration for extortion in addition to encryption
- Exfiltrates sensitive data
- Results in reputation impact for the organization
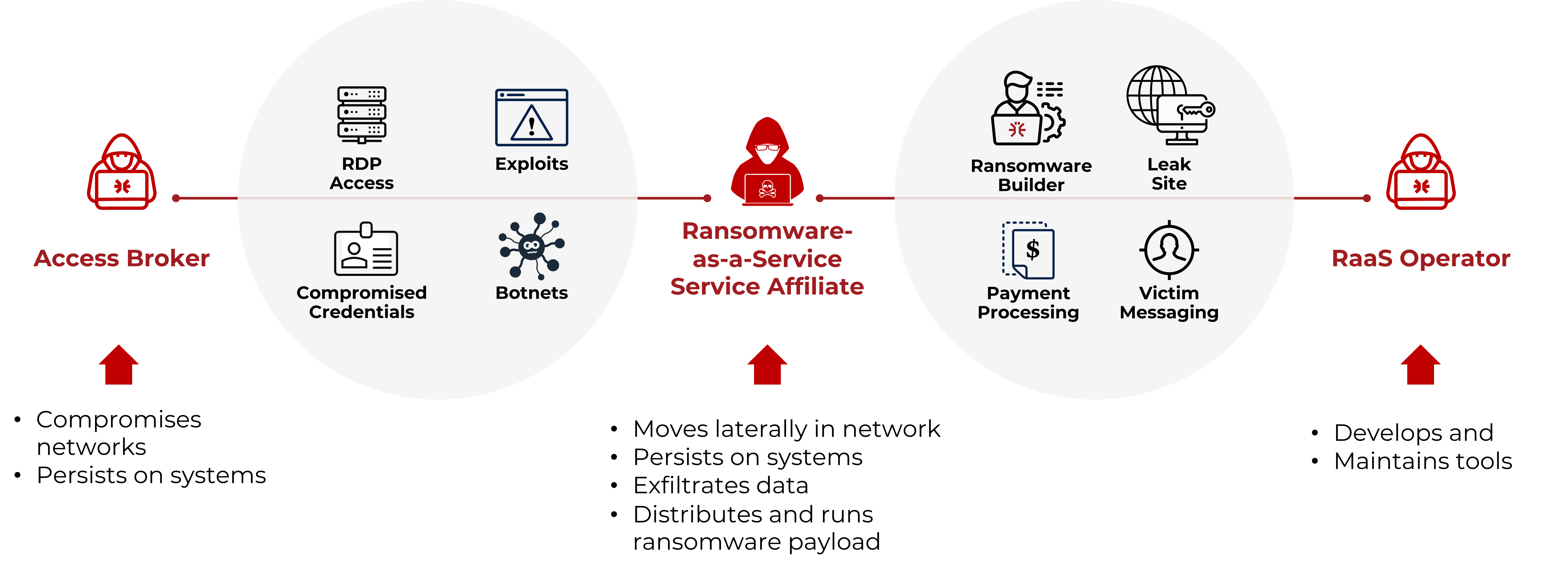
Ransomware-as-a-Service (RaaS) Model
RaaS is a decentralized model
How the RaaS affiliate model enables ransomware attacks
Modern Ransomware Bypassing Traditional Security Solutions
IABs provide initial access to endpoints without traditional security solutions
- Example: jump server with no EDR on it, providing a safe pivot point for attack actions
Ransomware using modern programming languages to evade signature-based detection
- Example: Alphv ransomware written in Rust as signature-based tooling is primarily focused on C/C++
Uses credentials to gain trusted access to resources
- Identity compromises such as Kerberoasting, accessing credentials from caches
Defense evasion to disable agent-based security solutions
- Escalate privileges and disable AV/EDR on endpoint

Ransomware written in Rust, to evade signature-based detection
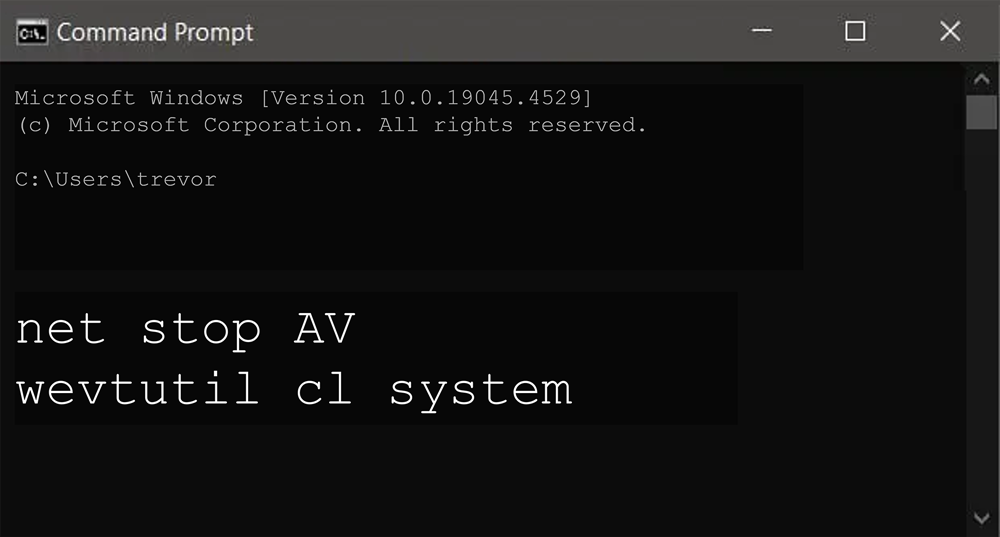
Defense evasion performed by Ransomware
Deception Detects Ransomware with Precision
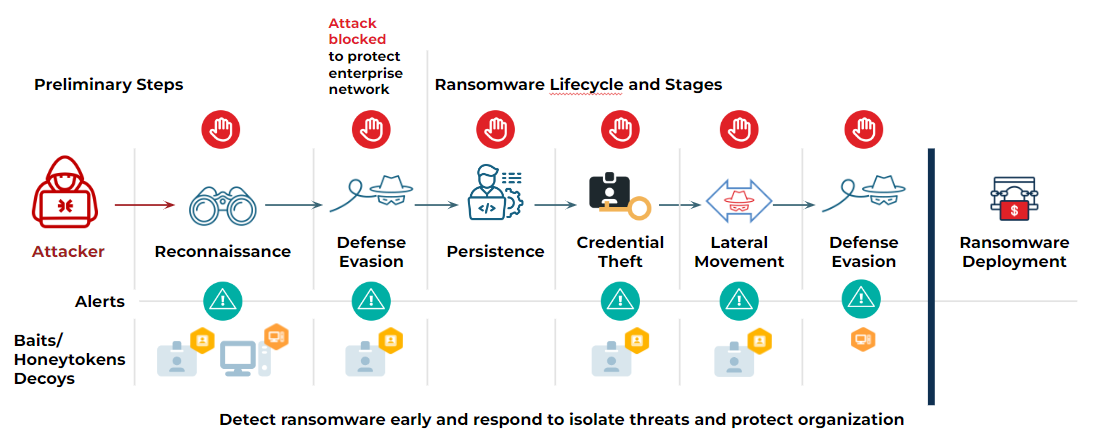
- Set traps based for each stage of the ransomware lifecycle
- Observe for activity against the traps
- Detect ransomware and raise alerts
Approach is agnostic to the ransomware variant and specific TTPs
- Independent of programming language, cryptographic algorithm, specific TTPs
- Works for known and unknown (zero day) ransomware variants
Enterprise-scale Deception for Ransomware Defense
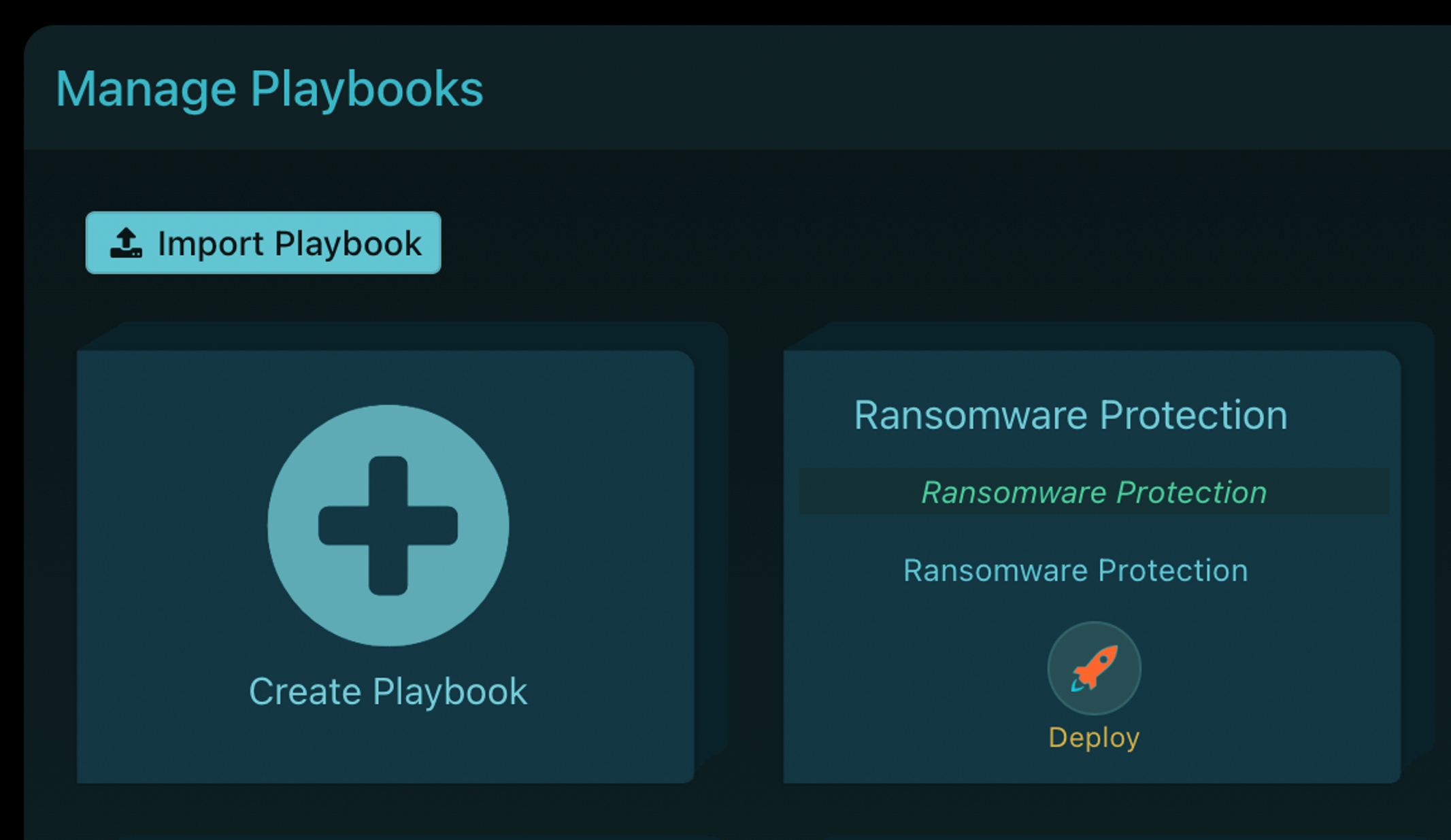
Acalvio provides a prepackaged ransomware protection playbook
Administrator imports the playbook and associates it to the relevant scope
ShadowPlex deploys purpose-built deceptions to detect ransomware early in the attack lifecycle
Automated deployment and refresh of deception across the enterprise
Alerts sent to SIEM and/or SOAR
- Single pane of glass for SOC teams
- MITRE mappings for standardized incident response
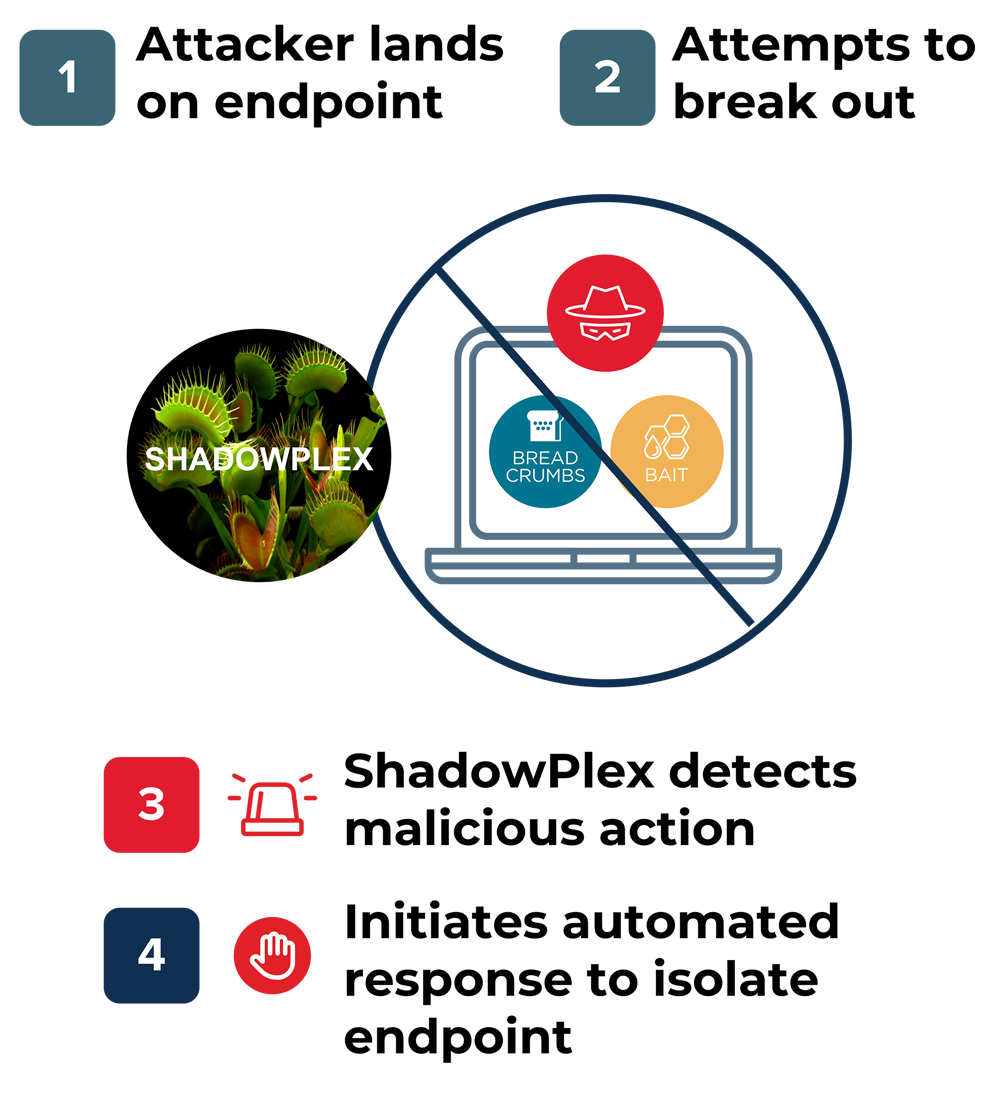
Response Policies to Isolate Threat
Response actions to isolate the threat
Leverages prebuilt integrations
Automated response to prevent ransomware breakout
Protects enterprise assets
Discover More
Learn how deception provides a necessary detection layer for early threat detection for endpoint security, network security, and identity security.
Defend Against Known and Zero-Day Ransomware
Join forces with Acalvio to defend against known and evolving ransomware variants. Stay protected as ransomware threats continue to evolve with novel variants emerging in the future.


