Overview
Cyber attacks are gaining in sophistication and stealth. Traditional security solutions are insufficient to defend against these stealthy threats. Cyber deception is a necessary layer for early and precise detection, protecting IT, OT, and Cloud environments from threats.
Modern Adversaries Bypass Traditional Security
Traditional security focused on detecting specific TTPs
Adversaries leveraging stealthy and evasive to bypass traditional security

Living Off the Land (LotL) Attacks
- Adversaries leverage existing OS utilities and tools to perform exploits
- Traditional security can’t distinguish between normal users and threat actors

Identity-driven Attacks
- Adversaries are targeting the identity architecture through identity exploits and exploits targeting cached credentials
- Traditional security solutions are unable to distinguish between legitimate and malicious use of credentials

AI-fueled Attacks and Zero Days
- Adversaries leverage AI to evade traditional security solutions focused on attacker TTPs
- Zero days exploits evade traditional detection methods

Supply Chain Attacks
- Injected malicious code corrupts software libraries and open- source software
- Leveraged whitelisting and implicit trust evades detection

Insider Threats
- Insider threats are particularly challenging to detect
- Privileged insiders have trusted access to critical systems and data
Organizations need to strengthen their cyber defense
Early and Precise Threat Detection Using Cyber Deception
Why ShadowPlex Advanced Threat Defense?
Agentless, scalable platform for enterprise-wide protection: protect IT, OT, and Cloud environments through a scalable platform
Deception Playbooks and AI for ease of administration: Automated recommendations for deceptions using AI, reducing administrative effort for deception deployment
Prebuilt integrations for interoperability: native integrations with EDR, XDR, SIEM, and SOAR for ease of adoption
Auto triaged detections that provide actionable intelligence for SOC: high fidelity alerts mapped to MITRE for standardized incident response
Packaged solutions for immediate time to value: support for prebuilt use cases to provide immediate value
Enterprise-scale deception with unmatched
ease of use
Patented architecture and innovation
DeceptionFarms architecture: distributed deception with centralized administration. Agentless deception deployment.
DeceptionFarm: Central component of the architecture.
Sensor: Lightweight component that projects decoys into target environment.
Sensor instances for IT, OT, Cloud environments.
Single instance supports deployment into multiple subnets.
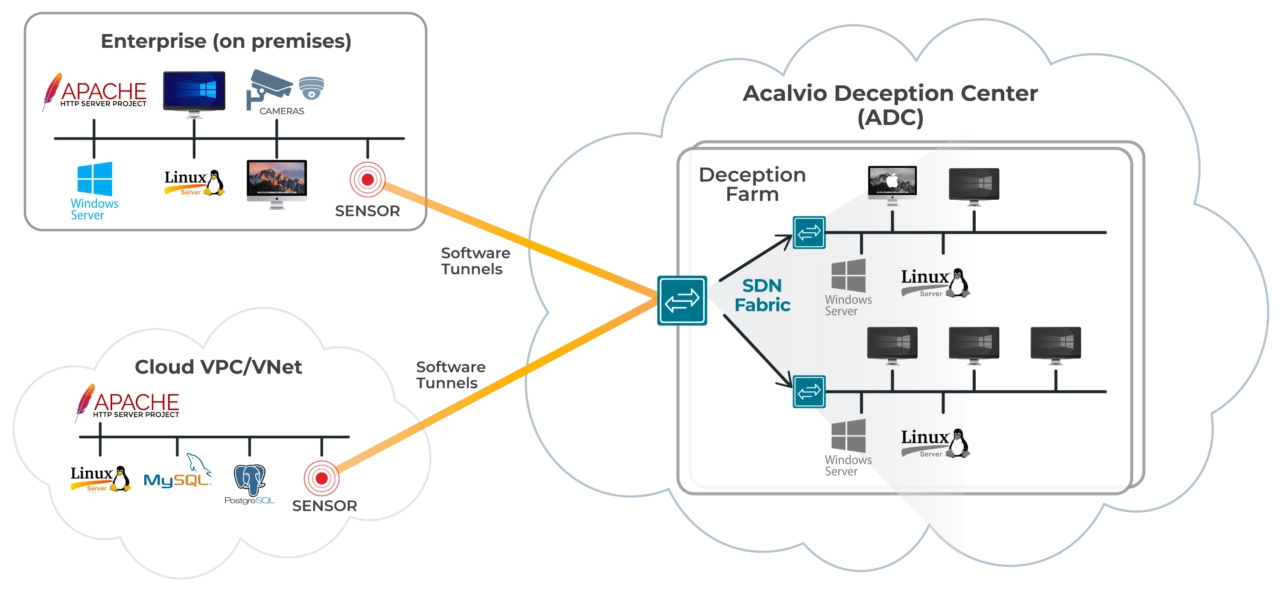
Agentless, enterprise-scale platform
Scalable for enterprise-wide protection: Adversaries can target any part of the organization. Deploying deception at scale provides early detection of threats. Agentless platform avoids management overheads associated with deployment of additional agents.
Reduced total cost of ownership: innovations to reduce third party software license costs for deceptions. Reduce resource requirements, providing significant savings in total cost of ownership (TCO).
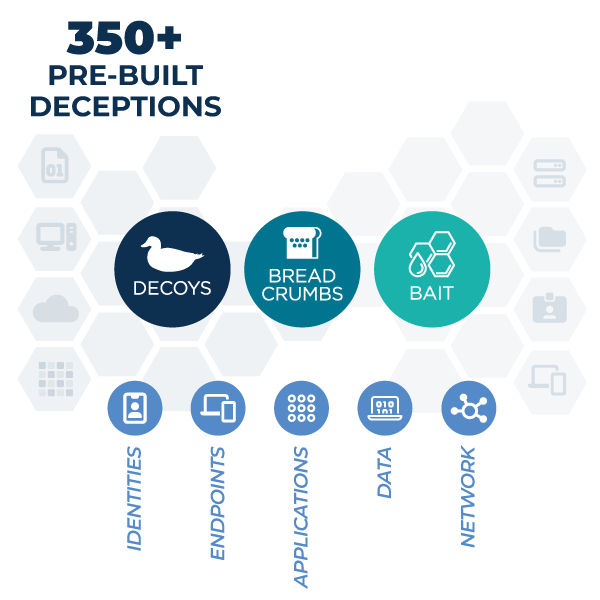
Comprehensive deception palette
Decoys: targets for attackers. Represent assets in IT, OT, and Cloud. Detect reconnaissance, lateral movement, vulnerability exploit attempts
Breadcrumbs: deceptive credentials and connection profiles. Lead adversaries to decoys and divert away from production assets. Detect endpoint compromise.
Baits: tripwires to detect adversarial actions such as exfiltration, defense evasion.

Deception Playbooks and AI for autonomous deception
Packaged solutions for immediate time to value: Playbooks encapsulate deception domain knowledge into a deployable artifact for immediate value.
AI for reduced administrative effort: AI algorithms automate deception recommendations, reducing administrative effort for configuring deceptions.
Actionable alerts enhance SOC efficiency
Auto triaged alerts to enhance SOC efficiency: AI automates triaging of deception events, surfacing clean, actionable detections to eliminate the deluge of alerts.
Automated response to isolate threats: High fidelity alerts enable automated response actions to isolate the threat and prevent attack propagation.

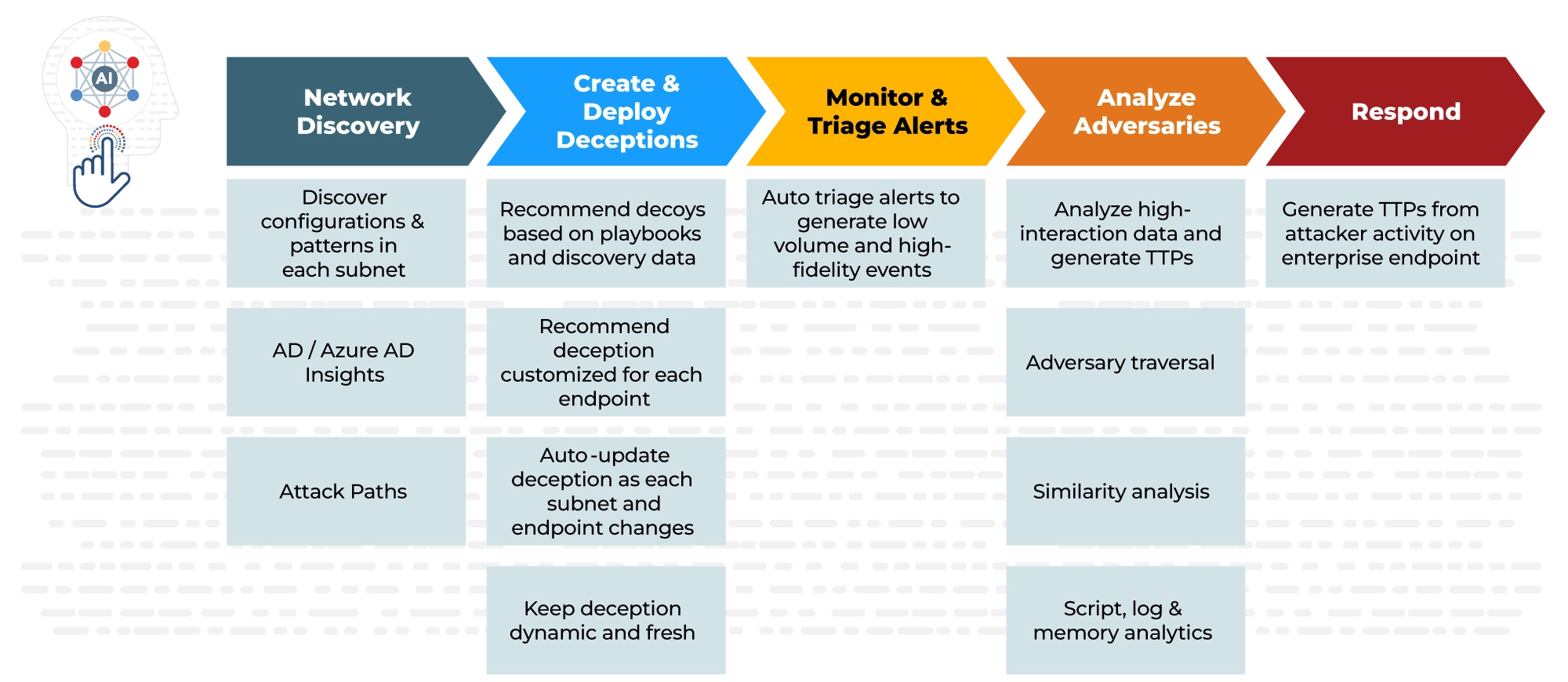
Deception Operationalized by Artificial Intelligence
AI Integrated into Every Step
Use Cases
Packaged Solutions for Cybersecurity Challenges

Early Threat Detection
- Adversary breakout times are significantly shorter
- Detect threats early in attack lifecycle, prior to adversary breakout

Insider Threat Detection
- Insider threats bypass traditional security
- Detect insider threats, including privileged insiders
OT Security
- OT assets are not compatible with traditional security
- OT security needs agentless, non-intrusive detection ability

Advance Zero Trust Maturity
- Assume breach is a key principle of Zero Trust
- Deception improves cyber visibility for threat detection to mature Zero Trust implementation

Detect Zero-Day Ransomware
- Detect known and unknown ransomware with precision
- Automated response to isolate the threat and protect the organization

Threat Hunting
- Active Threat Hunting based on cyber deception and analytics
- Identify latent threats and confirm hypothesis
Gain immediate value through packaged solutions for use cases
Flexible Deployment Options
Cloud to On-Premises
Easy deployment from your
favorite cloud provider
On-Premises to On-Premises
On-premises hosting of our cloud-scalable
deception platform
Cloud to Cloud
Protect cloud workloads with deceptions
delivered from the cloud
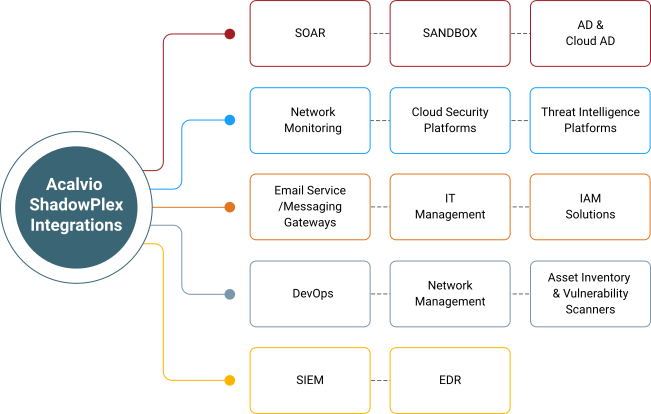
Prebuilt integrations
Native integrations with security platforms: prebuilt integrations with industry leading EDR and XDR platforms for agentless deception deployment and automated response actions.
SIEM and SOAR: deception alerts are sent to SIEM/SOAR to maintain the single pane of glass for SOC teams.
Email, Slack, Webhooks: notifications for administrator through multiple mechanisms
Discover More
Learn how Acalvio deception platform provides solutions for customer use cases. Explore our resources, including integration guides, solution briefs, and customer case studies, to tap into the tangible benefits of deception-based threat detection.
Adopt Proactive Cyber Defense
Join forces with Acalvio to fortify your defenses and safeguard your digital future. Reach out today to learn more about our industry leading deception platform and its role in early and precise threat detection to stop breaches.