
Available on the CrowdStrike Store, the integration empowers CrowdStrike customers to use Acalvio’s Honeytokens and Honey Accounts seamlessly to detect identity threats.
Identity-Based Attacks are on the rise
Identity threats are involved in 80% of all cyberattacks, according to the CrowdStrike 2023 Global Threat Report. The increased adoption of cloud services and remote work environments has increased the attacker’s emphasis on identity compromise.
Sophisticated attackers like APTs and ransomware actors typically start their campaign with an attack on identities. Attackers can exploit identities on endpoints, applications, and identity stores.
Protecting identities online is complex and combating threats requires a new class of identity security solutions.
Attackers can bypass Traditional Identity Security Solutions
Enterprises typically have prevention-based identity security solutions, such as PAM, IAM, and MFA deployed. These solutions offer their value for policy enforcement but are not focused on detecting identity threats.
There is a significant identity threat surface that is targeted by attackers. For example, service accounts represent an important identity threat surface. Service accounts are typically associated with higher privileges and are difficult to protect using MFA. PAM solutions have a long deployment window, and onboarding privileged accounts to PAM is a challenge.
There is a missing foundational element for the identity security stack that is focused on detecting and responding to identity threats. Gartner has called this Identity threat detection and response (ITDR).
Identity-driven attacks are difficult to detect using traditional detection mechanisms.
Traditional detection mechanisms such as log analytics and behavior-based detection techniques are not effective at detecting identity-driven attacks. Log analytics is slow and time-consuming, and logs are not always available.
As the CrowdStrike blog indicates, when a valid user’s credentials have been compromised and an adversary is masquerading as that user, it is often very difficult to differentiate between the user’s typical behavior and that of the attacker, using traditional security measures and tools.
Deception technology for Identity Based Security
Deception technology has been recognized by industry experts and identity security solutions researchers as a proven mechanism for identity threat defense. Deception provides high-fidelity detection of identity threats, is agnostic to the specific offensive technique, and does not have any dependency on logs or signatures.
How are Honey Accounts and HoneyTokens used in Deception Technology?
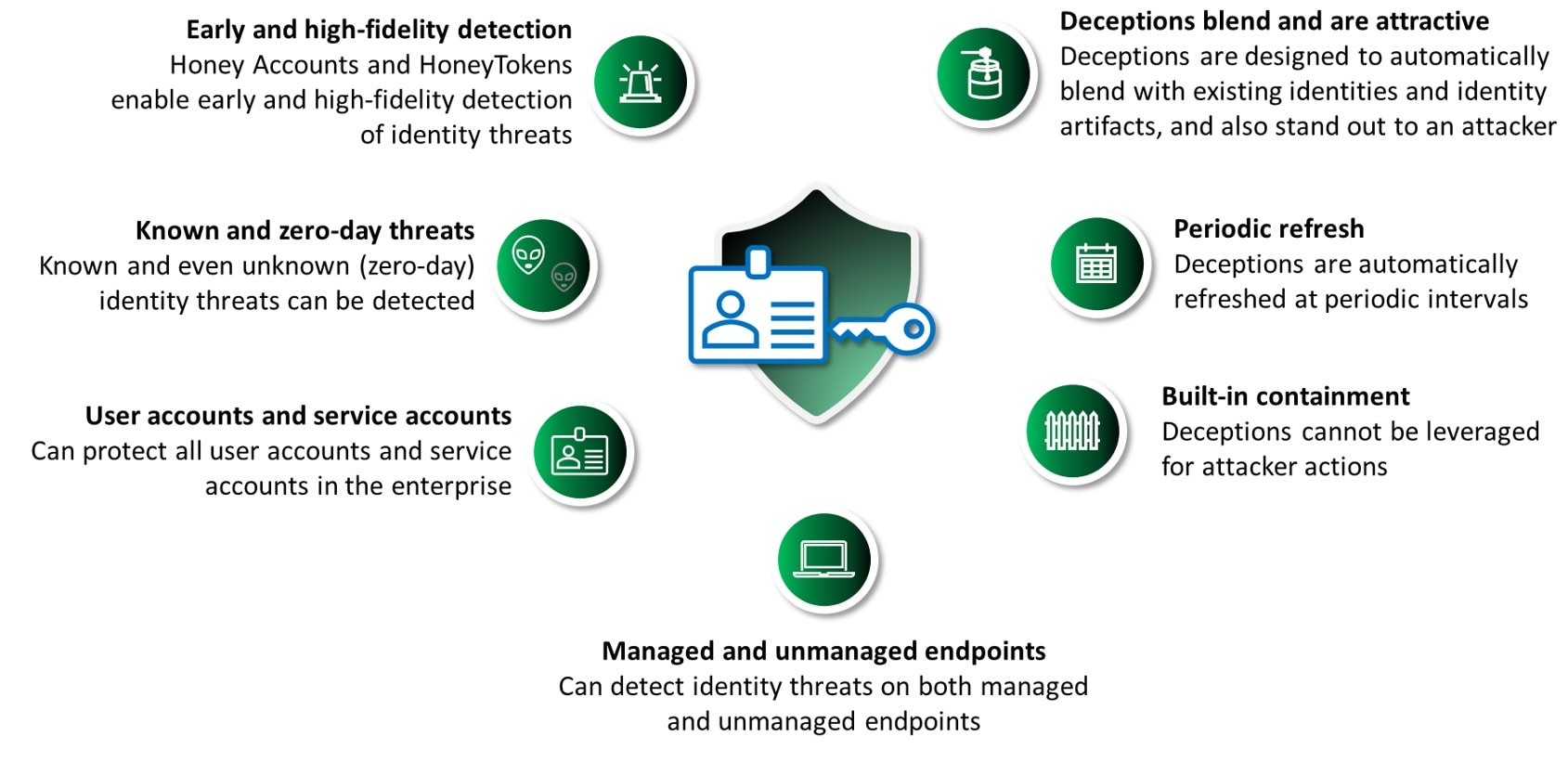
Honey Accounts are deceptive accounts (representing human and service accounts) created in the Active Directory (AD) that are specifically designed to lure attackers and deflect them away from real identities.
HoneyTokens are deceptive credentials and data that are embedded in legitimate assets such as endpoints and cloud workloads. Any usage or manipulation of these deception artifacts is a very reliable indicator of an identity threat.
Operationalizing Honey Accounts and HoneyTokens
Operationalizing Honey Accounts and HoneyTokens requires a deep domain knowledge of deception technology and a mature and scalable platform. Enterprise security administrators attempting to create Honey Accounts manually need to make several decisions:
- How many AD accounts to create in each domain?
- What kind of accounts to create?
- How to blend and make accounts appear legitimate?
- How to make AD accounts fingerprint resistant?
- How to “lure adversaries away” from critical resources?
- How to manually flag multiple AD accounts as honey accounts?
Deploying and refreshing HoneyTokens at scale across a large number of endpoints cannot be done manually. IT automation also cannot solve this issue, as oneyTokens need to be created based on deep domain knowledge of deception technology, for the solution to be effective.
This makes it abundantly clear that enterprises must have a platform to operationalize Honey Accounts and HoneyTokens for effective identity security solutions.
The Solution
The integration (now available on the CrowdStrike Store) enables CrowdStrike customers to use Acalvio’s automation and AI-based recommendations to quickly create and deploy HoneyTokens and Honey Accounts through CrowdStrike Falcon® Identity Protection.
Acalvio recommends the count and types of Honey Accounts that can be registered on CrowdStrike. Acalvio also deploys HoneyTokens on endpoints. CrowdStrike monitors the activity on Honey Accounts and effectively blocks the identity threat based on that information. This identity security solution is scalable and can be used to protect managed and unmanaged endpoints.
ShadowPlex leverages advanced AI algorithms to recommend Honey Accounts and HoneyTokens that are made attractive to attackers, blended with the target environment, and invisible to users. ShadowPlex performs automated deception refresh cycles to keep them fresh and realistic to attackers.
Key Solution Benefits
- The integration is scalable and supports the ability to deploy across multiple AD domains and many endpoints.
- The identity security solution is easy to adopt and does not require any additional component to be installed in the customer environment.
- The solution protects managed and unmanaged endpoints from identity threats.
- The Cloud service ensures continuous value and ease of adoption.
By integrating Acalvio’s expertise into the CrowdStrike platform, customers gain access to an augmented defense-in-depth strategy that can swiftly adapt to emerging threats.
With Honey Account and Honeytoken capabilities, organizations can lure and divert attackers away from actual identities and sensitive assets. The Acalvio identity security solution also offers seamless deployment and efficient lifecycle management of advanced and fingerprint-resistant deceptions across enterprise endpoints.
Read more about Acalvio Honeytoken Accounts and Honeytokens for CrowdStrike Falcon® Identity Protection. Watch a short video overview. To find out how Acalvio ShadowPlex can protect critical identity assets in your organization, schedule a demo. Or contact Acalvio at info@acalvio.com.


