
CrowdStrike® Trusted Partners’ solutions go beyond simple integrations.
Our partnership with CrowdStrike not only makes Deception easy to deploy for CrowdStrike customers, but also introduces a powerful new capability – Deception-based Active Threat Hunting.
The CrowdStrike Falcon® platform offers next-generation endpoint security with an intelligent, easy-to-install lightweight agent. ShadowPlex Autonomous Deception Solution uses the Falcon agent for simplifying all aspects: deploying deceptions, detecting malicious activity, engaging with the adversary and enacting timely and appropriate response.
- Deployment of breadcrumbs and baits on endpoints is now completely autonomous.
- Detection to track access to breadcrumbs – attack is detected not when breadcrumbs are used, but even when breadcrumbs are accessed. This is the big advantage of having the Falcon agent on the enterprise hosts watching who accesses the carefully hidden breadcrumbs.
- Response – to quickly isolate a compromised system.
The Falcon platform stores the rich data collected from the enterprise hosts in the CrowdStrike Threat Graph®. The platform also includes a sandbox – CrowdStrike Sandbox that performs deep analysis of evasive and unknown threats. We leveraged these technologies to provide a new threat hunting capability.
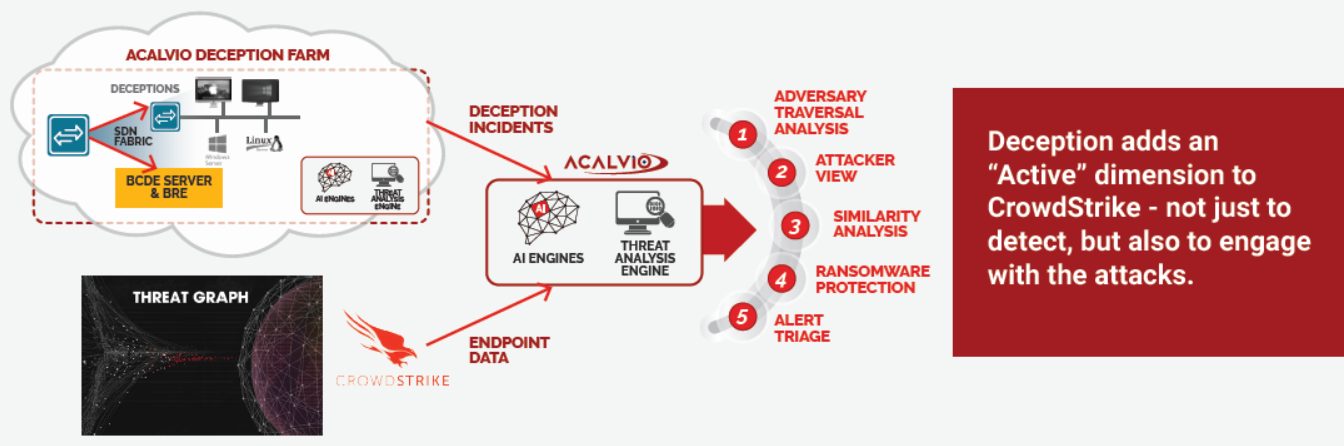
Deception-based Active Threat Hunting empowers IR teams in the following areas:
- Adversary Traversal Analysis: When an attack interacts with a decoy, we identify the source as a compromised host. The Threat Hunting capability uses the data from the Threat Graph to trace the attack deep into the enterprise network. We start from a deception incident and walk back by mining the data from the Threat Graph and using AI techniques, to come up with the list of all hosts compromised along the attacker’s path to the decoy
- Attacker View: CrowdStrike collects detailed data from each enterprise host. Based on the deception incident and data in Threat Graph, ShadowPlex builds comprehensive adversary indicators of attack (IOAs).
- Similarity Analysis: The IOAs generated are to proactively identify machines susceptible to observed exploits or already compromised.
- Ransomware Protection: Deception-based precise detection and rapid engagement of ransomware to complement the CrowdStrike machine-learning-based protection.
- Alert Triage: New workflows are built for active threat hunting to expose latent threats. Analysts can do hypothesis testing by creating deception targeting specific threats.
Acalvio ShadowPlex cloud-delivered deception integrates with and perfectly complements CrowdStrike’s cloud-delivered endpoint protection. Organizations can try, buy and deploy ShadowPlex from the CrowdStrike store. The partnership provides customers not only better deception that is easier to deploy, but also a powerful new threat hunting capability. Visit our Crowdstrike store here.


