
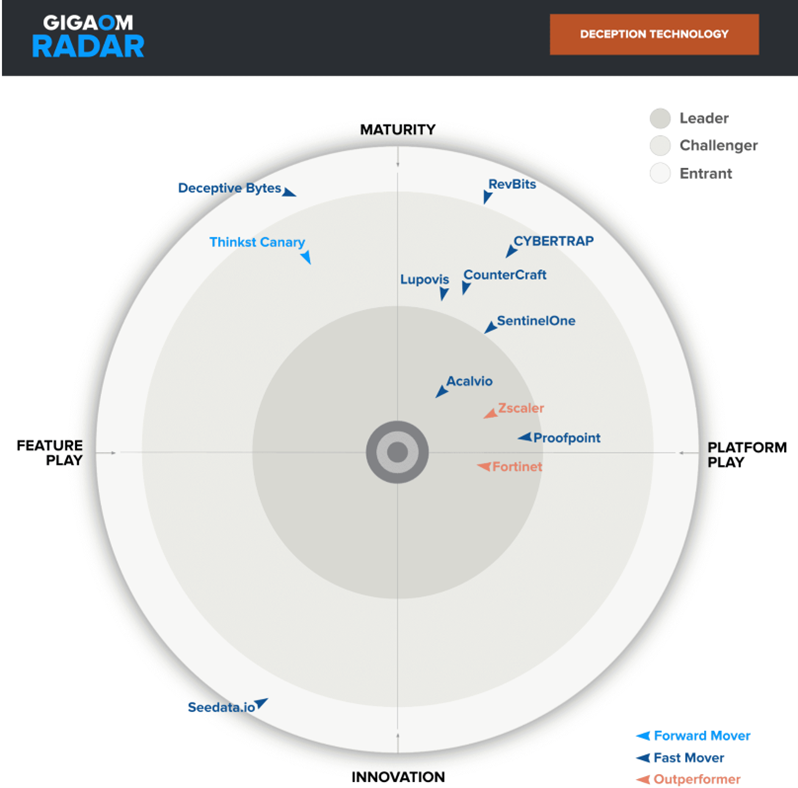
GigaOm’s recently published Radar chart on cyber deception platforms for 2024 provides detailed comparison of leading deception vendors. The research involved a set of key business criteria for deception solutions and considers the requirements of different market segments.
Why deception technology is a strategic imperative
With adversaries becoming increasingly sophisticated and stealthy, security teams need rapid threat detection abilities coupled with their response actions to isolate potential threats before they spread through a network. Cyber attacks are bypassing traditional security solutions and are resulting in large-scale breaches. A defense-in-depth approach to cybersecurity combines prevention-based security controls with a set of interlocking, non-overlapping detection layers to protect critical assets, identities, and sensitive data. Deception technology is an integral detection layer that enables a proactive approach to threat detection and an effective solution to current and evolving threats.
ShadowPlex balances technology leadership with simplicity of deployment
We are thrilled that the ShadowPlex has been rated a leader for the second year in a row by the GigaOm Radar report.
Acalvio scored the highest in each of the business criteria evaluated, which highlights the significant set of unique advantages, built on 26 issued patents, in ShadowPlex.
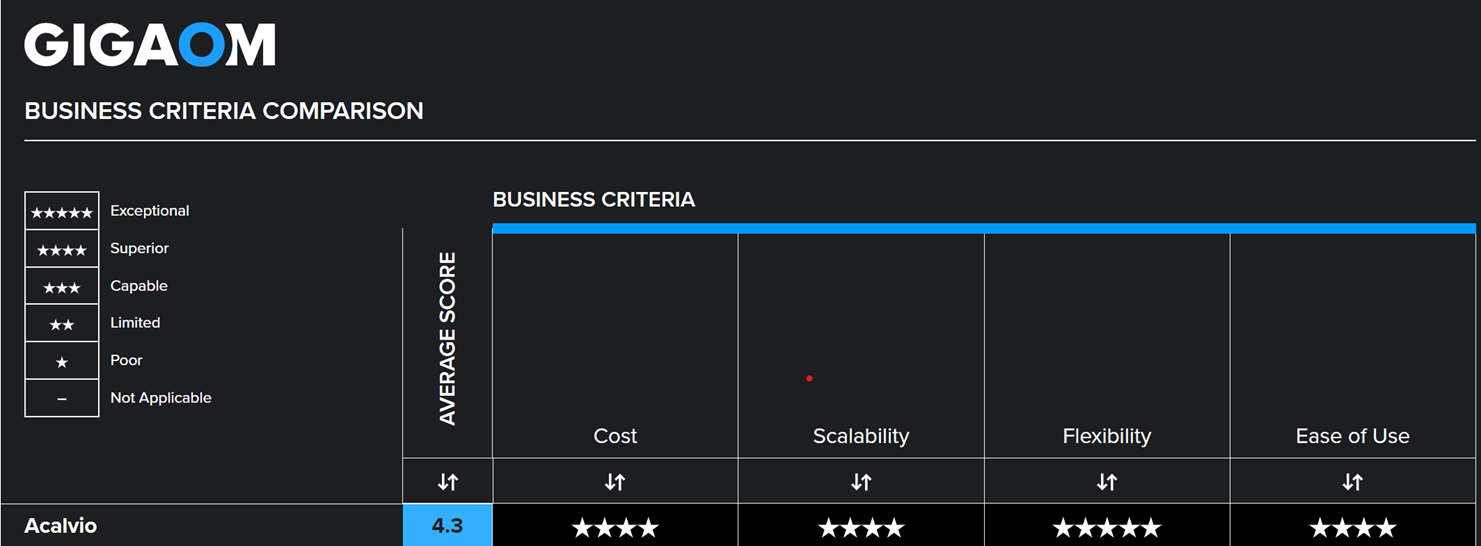
Scalability
- Deception Farms architecture with a lightweight sensor enables deception deployment at scale with minimal infrastructure requirements.
- Built-in orchestration capabilities for automated and agentless endpoint deception deployment and refresh. This enables endpoint deceptions to be deployed across a large set of endpoints.
- Patented innovations (fluid deception, reflection technology) to enable a large number of decoys to be projected to deploy deceptions at enterprise scale.
- Administration designed for deployment at scale. This includes the concept of sites, a logical construct that enables subnets to be grouped into a higher-level construct.
Flexibility
- Deceptions for on-premises, cloud, kubernetes, OT, and IoT environments.
- Support for deceptions at multiple levels of interaction/engagement, enabling defense teams to detect and engage with the adversary based on the use case.
- Extensive palette of deceptions, with decoys, breadcrumbs, baits, honey accounts and honeytokens to provide a comprehensive set of deceptions.
- Ability to customize the deceptions based on enterprise-specific content and templates.
- Ability to deploy multiple types of deception strategies from a single platform, providing flexibility to incorporate the requirements of a complex organization.
Ease of use
- Deception Playbooks for pre-packaged solutions for deception, providing immediate time to value and improving operational efficiency.
- Agentless endpoint deception deployment and refresh to avoid deployment challenges associated with the deployment of additional agents.
- Built-in automated triaging of deception alerts to provide actionable intelligence for the SOC and to avoid manual alert correlation or deduplication.
Cost
- Patented innovation, fluid deception, reduces the third-party OS and application licensing cost.
- AI algorithms for automated deception recommendation and placement and deception deployment reduce the manual effort for administrators, reducing the overall cost of managing the platform.
- Pre-integrated with security solutions, avoiding the need for field programming that can increase the overall cost of adoption.
Acalvio ShadowPlex also scored the highest in both the two emerging features – Cloud-native deception and Adversarial AI countermeasures.
Summary
The GigaOm Radar report emphasizes the critical importance of deception technology for the protection of organizations from sophisticated threats. The report takes a deep dive into the technology and provides a well-researched analysis of 12 deception solutions. With Acalvio ShadowPlex receiving high praise for its mature and robust capabilities along with cost-effective solutions, it’s your winning choice for a deception-based detection layer to complete a defense in-depth approach to cybersecurity.


