Acalvio Threat Labs
Shamoon is one of the critical threats that has been able to penetrate traditional defenses successfully not once, twice, but thrice – in 2012, 2016 and 2017. The main purpose of Shamoon Threat Actor was the destruction of the endpoint computers by wiping the Master Boot Record (MBR), rendering them unusable. If malware infects the end point, the effect is limited only to the infected end point. Since Shamoon can spread across the internal network, the scope of it’s destruction is not limited to the infected endpoint, but can affect machines in the same subnet. Shamoon erased data on 75% of Aramco’s corporate PCs[1]. The first section of this blog covers an in-depth technical analysis of the lateral movement technique used by Shamoon. Since Shamoon has been able to penetrate the traditional defenses multiple time, the second section discusses a detection architecture that can be used to detect catastrophic attack like Shamoon.
Lateral Movement by Shamoon
Shamoon runs as a service and attempts to spread to other hosts on the subnet. Once the endpoint is infected by Shamoon, it spawns 3 general functionality threads for SMB network enumeration and spreading, command and control, and running the disk wiper module.
Spreading across the Network is performed via local subnet enumeration (/24 subnet) with multiple credentials (3 sets) and share locations (4 locations). As a part of first step, the malware inherits the IP address of the infected machine.

Figure 1.0 Network IP Address Iteration of Shamoon.
As shown in figure 1.0, it then loops over the 4th IPv4 octet, starting from 0, skipping its own IP and ending with 254, thus making an attempt to spread across every computer in the sub-net.

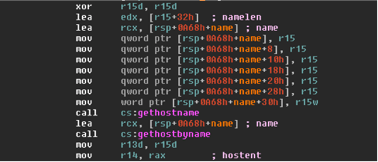
Figure 2.0 Showing the Operation Mode in Shamoon.
As shown in figure 2.0, Shamoon has a hard-coded operational mode flag, “F” or “S” set at compile time to determine fast or slow mode of operation. As shown in figure 3.0, in the fast mode, the malware spawns threads for each IP address. In slow mode it will synchronously spans each IP address waiting for each network call to either succeed or timeout before moving to the next IP address.

Figure 3.0 Showing the fast and Slow mode of Shamoon.
For each IP address, the malware attempts a set of credentials to get access to the machine which are shown in Table 1.0.
| Usernames: | ‘gacaadmin15’, ‘gacaadmin22’, ‘gacaadmin08’, ‘Administrator’ |
| Passwords | ‘hggiH;fv1122’, ‘@ftsEnterprise02’, ‘P@ssw0rd@Evotnc5581’, ‘P@ssw0rd’ |
| Domains | ‘GACA’, ‘GACA’, ‘GACA’, ‘GACAANS’ |
Table 1.0 Showing the list of Credentials and Passwords used by Shamoon.
For each set of hard-coded credentials, the malware attempts a connection with each hard-coded remote share location listed below:
-
- C$\WINDOWS
- D$\WINDOWS
- E$\WINDOWS
- ADMIN$

Figure 4.0 showing the username and passwords.
As shown in figure 4.0, attempt to connect to the machine using the hard coded username and password is performed by first checking RemoteRegistry service on the target is running, and then disabling UAC through a registry key
- SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System\LocalAccountTokenFilterPolicy
After the remote registry check and UAC disable attempt, NetUseAdd is called for the credential set and share location.

Figure 5.0 Code snippet which shows the Registry Disabling attempt of Shamoon
If the NetUseAdd call fails or times out, the malware attempts the next remote share / credential set. If the NetUseAdd call succeeds, the malware continues spreading by calling Windows API functions to copy itself to \system32 directory. Once it has copied the file in the machine, it then dynamically invokes the Windows function “NetScheduleJobAdd” and schedules a remote task on the target system to run the dropped file. Thereafter, as shown in figure 7.0 it deletes the remote job after 95 seconds.

Figure 6.0 code showing the scheduling of Service.

Figure 7.0 code showing the deletion of the service.
Why Deception-based is ideal to detect Shamoon?
Traditional prevention mechanisms, either network inline or endpoint, can be classified into two categories:
- Deep scanning of a file to extract its feature set, then through the use of machine learning, probabilistic, or heuristic algorithms, the file is classified as either malicious or benign.
- The second category of detection architecture uses a virtualized environment for detonating a file in order to classify the file as either benign or malicious.
These two detection architectures can be used to detect new variants. However, both these approaches can be evaded by threat actors. The following is an example of an evasion: if the malicious payload gets delivered via a new file format, then a new set of features might have to be extracted for the file format and a new algorithm might have to be developed. Similarly, for the second approach employing detonation of a file in a virtualized environment, the environment might have to be updated to ensure the new file format gets detonated and the virtualized environment has appropriate instrumentation to capture the true behavior of the file. Development and deployment of detection algorithms for the new file formats carrying a malicious payload will require time, and therefore will open a window of opportunity for the threat actor to exploit the organization.
A deception-centric detection architecture, deploys distributed deception across the network and on the endpoint. During the execution of a worm like Shamoon, the worm will perform various activities, like: spreading across the network, making a copy of itself, starting a job, deleting a job, deleting the MBR, etc. These activities will trigger the distributed deception sensors, raising an alert. Through the alert, the infected endpoint is identified and can be quarantined. Thus, unlike traditional security architectures that use deep scanning of files or virtualized environments, a deception-centric architecture provides an inherent advantage: It is independent of the delivery vector employed by a threat actor to deliver the malicious payload.
Conclusion:
Shamoon infected three quarter of Aramco’s computers. This catastrophic effect can bring any corporation to its knees. Traditional security architectures employing virtualized machines for detonation or deep scanning of a file can be evaded by a threat actor. These evasion techniques can open a window of opportunity to exploit an organization. A deception-centric architecture gets triggered during the actual execution of malware. Consequently, we recommend a deception-centric detection approach to defend an organization against worms like Shamoon .
References :
In Cyberattack on Saudi Firm, U.S. Sees Iran Firing Back
IOC of the malicious files.
- 47bb36cd2832a18b5ae951cf5a7d44fba6d8f5dca0a372392d40f51d1fe1ac34 (X64 dropper)
- 394a7ebad5dfc13d6c75945a61063470dc3b68f7a207613b79ef000e1990909b (X86 Dropper)
- 772ceedbc2cacf7b16ae967de310350e42aa47e5cef19f4423220d41501d86a5 (X64 Command Module)
- C7fc1f9c2bed748b50a599ee2fa609eb7c9ddaeb9cd16633ba0d10cf66891d8a (X64 Wiper Module)


