The previous post in the Identity Security blog series covered identity-based attacks and why there has been an increase in the number and types of such attacks.
This blog describes the identity security ecosystem. The blog covers the components of an identity security ecosystem, what each component does in an enterprise, and describes some limitations.
In any enterprise, there is an existing ecosystem for identities and their management. Starting with the identity repositories, authentication, and access policies, and covering the trust relationship definitions at macro and micro levels. Organizations have multiple solutions in place for managing this ecosystem.
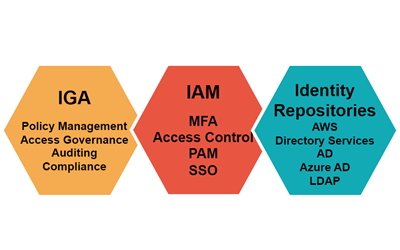
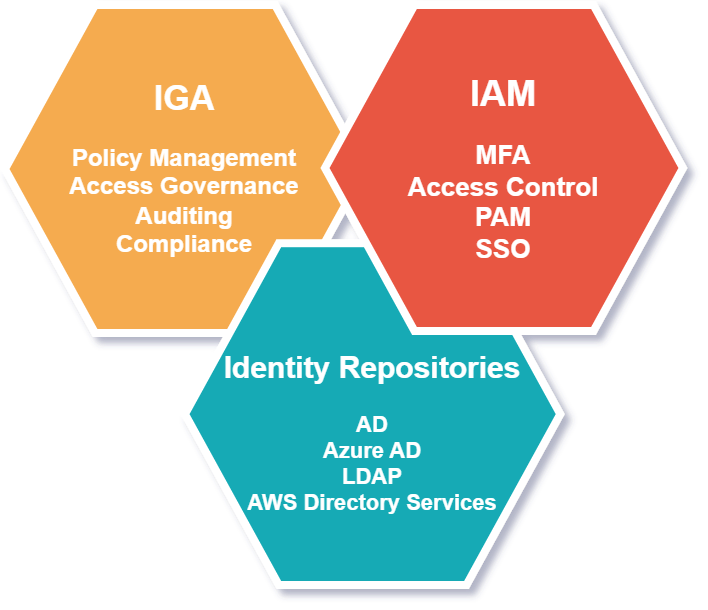
What are the Components of an Identity Security Ecosystem?
The three major components of an identity security ecosystem are:
- IGA – Identity Governance and Administration
- IAM – Identity and Access Management
- Identity Repositories – such as Active Directory and Azure AD
What is IGA (Identity Governance and Administration)?
One of the most important components of the identity security ecosystem is Identity Governance and Administration, or IGA. This is particularly important for large organizations. Enterprises implement IGA to control access and mitigate risk by automating user account creation and the management of user accounts, roles, and entitlements.
Companies use IGA to streamline onboarding, offboarding, employee movement, policy management, access governance, and other identity security measures. IGA can be envisioned as a lifecycle management system for identity. It is used to manage access to resources across on-premises assets, SaaS, and cloud-based applications.
The use of automation and centralized policy management strengthens security and reduces identity risk. For example, the various roles can be defined and managed in IGA, and a password policy can also be defined and managed through IGA. Another important function of IGA is auditing governance and compliance reporting. For example, access requests to resources are handled by IGA to ensure governance and auditing.
What is IAM (Identity and Access Management)?
Identity and Access Management or IAM is the management of access to systems and resources. Its earliest days are best represented by Microsoft’s Active Directory or AD service. AD was one of the earliest tools to keep track of access to PCs, and applications, and eventually, it expanded into managing access to mail systems and other IT resources.
There has been a heavy push for IAM services to be delivered from the cloud. One of the limitations of AD was that it was only available within local or enterprise networks. That changed as IT resources moved out of the internal enterprise domains into the Internet and cloud services became the norm. To take advantage of this shift, new types of cloud-based IAM services were developed and became popular.
What does IAM include and what are the limitations?
IAM includes many capabilities, such as password authentication and a more secure form of authentication known as Multi-Factor Authentication (MFA). Authorization, also known as Access Control, is also a part of IAM.
IAM falls short in the ability to understand what users can do once they gain access to an application. It’s one thing to get access to the applications, but controlling what a user can do once they get access to the application is a challenge. For example, whether a user can access a database or is neither governed by IGA nor enforced by IAM. But controlling what the user can do once they log in to the database, is outside the scope of traditional IAM offerings.
Where does PAM (Privileged Access Management) fit in?
PAM is a specific type of access control meant for privileged users. Since attackers are interested in compromising privileged accounts like administrator accounts, a special type of identity offering was required. The goal is to secure access for privileged accounts by password vaulting, besides session recording for compliance reasons.
What about Single Sign-On?
Single sign-on and federation are also part of IAM. IAM components ensure that identity is verified by authentication, access to resources is controlled, and consistent with the policies using RBAC (Role-Based Access Control).
Single sign-on or SSO means that users do not have to authenticate each time they want to access a resource, making it convenient for the users. MFA provides additional verification for an identity trying to access a resource.
What are identity stores?
Identity stores, or identity repositories, make up another component of the identity security ecosystem. This is the data store where all the identities and related information such as groups, and policies are stored. Active Directory AD, Azure AD, JumpCloud, LDAP, and AWS Directory Services are all examples of an identity store.
How do IGA and IAM work together?
Identity Governance and Administration (IGA) and Identity and Access Management (IAM) work in concert to control access to resources, prevent data breaches, and comply with regulations. IGA can be thought of as a higher form of IAM because it provides more granular access to applications.
Once a user is in an application, IGA controls what the user can do within the application. As an example, a simple user role can only access basic functionality, but an administrator role can manage the application itself. What a user can do based on their role is called entitlements.
In highly regulated industries such as healthcare and financial services, it becomes even more important to track what users have been given access to within applications that might have personally identifiable information (PII). Governments mandate that firms protect this information and companies must keep records of which users have access to PII. Even more important is removing accesses for users who leave the firm. To manage and report these access details, firms use identity governance and administration capabilities.
What are the identity threat detection capabilities of these components?
There is no component whose primary function is to detect threats against identities. Gartner identified this missing component and called it ITDR or Identity Threat Detection and Response. Another critical component missing in the current Identity security ecosystem is attack surface management. While threat detection and response capabilities are useful and required, it is always better to prevent or reduce the attack surface.
There are many ways to implement ITDR, including deception technology. Advanced solutions such as Acalvio ShadowPlex offer both ITDR and attack surface reduction capabilities for enhanced identity security.
The next blog in the series covers practical issues that defenders face with rolling out PAM and MFA solutions.


