US Cert recently issued notification regarding malicious cyber activity by the North Korean government [1] as Hidden Cobra. There are two families of malware used by the North Korean Government.
- Remote Access Tool (RAT) known as Jonap
- A Server Message Block (SMB) worm called as Brambul worm.
As per the report by US-Cert, threat actor have been using these malware since 2009 to target multiple victims globally and in United States,- including the media, aerospace, financial, and critical infrastructure sector.
In this blog we share the technical details of the spreading techniques used by the Brambul worm and its detection by distributed deception platform.
Brambul Worm
The worm invokes multiple thread which then randomly generates the IP addresses for infection.

Figure 1.0 Showing the code for random generation of IP address.
Once the victim’s IP addresses, have been generated it connects to \\IPC$ share, on the port 445 of the victim machine with Administrator as the username and fixed hardcoded passwords.
Later down the malware code, it makes call to the WNetAddConnection2 API to connect to a network resource and constructs the below command.
“cmd.exe /q /c net share admin$=%%SystemRoot%% /GRANT:%s, FULL”
It then make call to the service manager. OpenSCManagerA() with the victim machine machines on the network as the parameter. StartSeviceA() is then called with the with the command as the parameter, will execute the command which will grant full permission on the remote machine. Once the command has been executed, the code will make call to DeleteService() which will then delete the service.
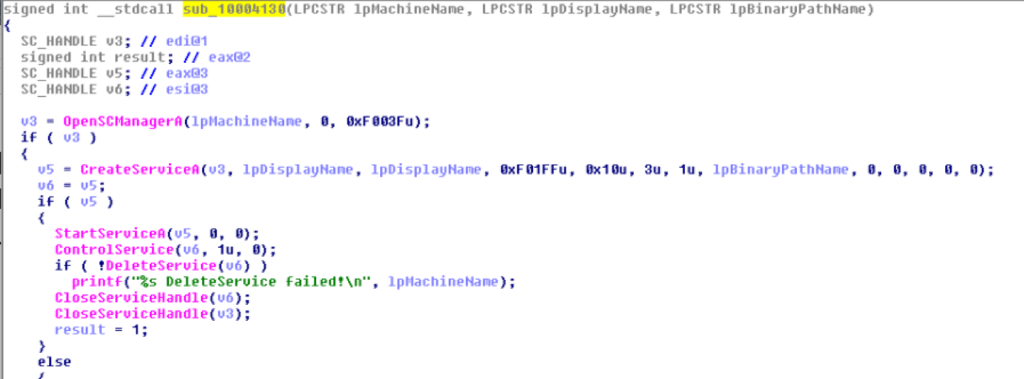
Once the full permission is granted on the remote machine, the worm is copied to the remote machine.
Detection by Distributed Deception Platform
The worm as such is not quite sophisticated and primarily relies on the brute force attempts. This will be successful only in weak environments. If the deception are deployed in a threat agnostic manner as discussed in the previous blog, network enumeration by the Brambul Worm will get detected by the distributed deception platform. Brute force condition will raise an alert of breach leading to the isolation of the infected endpoint.
References:
[1] Hidden Cobra – North Korean Malicious Cyber Activity. https://www.us-cert.gov/HIDDEN-COBRA-North-Korean-Malicious-Cyber-Activity
[2] HIDDEN COBRA – Jonap Backdoor Trojan and Brambul SMB worm https://www.us-cert.gov/ncas/alerts/TA18-149A


