Identity based attacks are rising dramatically. According to Verizon’s 2022 Data Breach Investigation Report, credential-based attacks have become the top path for threat actors to reach enterprise information assets. Microsoft estimated that they blocked almost 26 billion identity attack attempts in 2021. Similarly, Akamai estimates 193 billion credential attacks were blocked in 2020.
As more organizations transition to the cloud and a work-from-anywhere model, securing the enterprise network against identity threats is vital. A comprehensive Identity Threat Detection and Response (ITDR) solution is the best defense against identity attacks.
What is Identity Threat Detection and Response?
Identity Threat Detection and Response (ITDR) involves:
- Gaining visibility into the identity attack surface area of an enterprise network.
- Using that data to reduce the attack surface.
- Detecting and responding to identity attacks.
Advanced cybersecurity solutions like Acalvio ShadowPlex offer both Attack Surface Management and advanced Identity Threat Detection and Response capabilities.
Why is (ITDR) important?
What makes Identity Threat Detection and Response (ITDR) different from other types of solutions?
ITDR solutions are more proactive than traditional EDR or XDR solutions. ITDR solutions focus on identities, identifying misconfigurations, overprivileged identities, and several other identity-specific vulnerabilities. Security teams can use this data to reduce the potential attack surface that is available to attackers.
As organizations move towards implementing zero trust security models, secure credentials are a prerequisite. ITDR then becomes an important component of a zero trust implementation. Some ITDR solutions like Acalvio ShadowPlex use deception technology to detect and respond to identity threats. Deception technology is ideally suited to detect new and emerging threats since it does not rely on identifying defined patterns and anomaly detection, like conventional cybersecurity solutions.
ITDR in Today’s World
In research conducted by the Identity Defined Security Alliance, 84% of responding organizations said their organization had experienced an identity-related breach in the past year. The recent SolarWinds hack where attackers were able to evade detection for up to a year by mimicking legitimate traffic shows that identity attackers are employing more sophisticated techniques.
Conventional security solutions are not enough to stop such advanced identity attacks. With increasing identity-based attacks, dedicated Identity Threat Detection and Response solutions are indispensable in today’s world.
Types of Identity Threat Vulnerabilities
Some vulnerabilities that leave enterprise networks open to identity attacks include:
Over permissioned accounts
These include user and service accounts with significantly more privileges than required to perform certain tasks, accounts that can modify protected groups, and accounts with access to service account credentials.
Misconfigured accounts
These include Domain Administrator accounts with expired passwords, service accounts that are a part of Domain Admin groups, accounts with password set to never expire, accounts without multi-factor authentication enabled, and shadow admin accounts.
Inactive accounts
These include inactive privileged user and service accounts.
In addition, other significant vulnerabilities such as misconfigured mailboxes, certificate templates, and kerberoastable accounts all provide potential attack paths for identity threats.
Acalvio Identity Threat Detection and Response
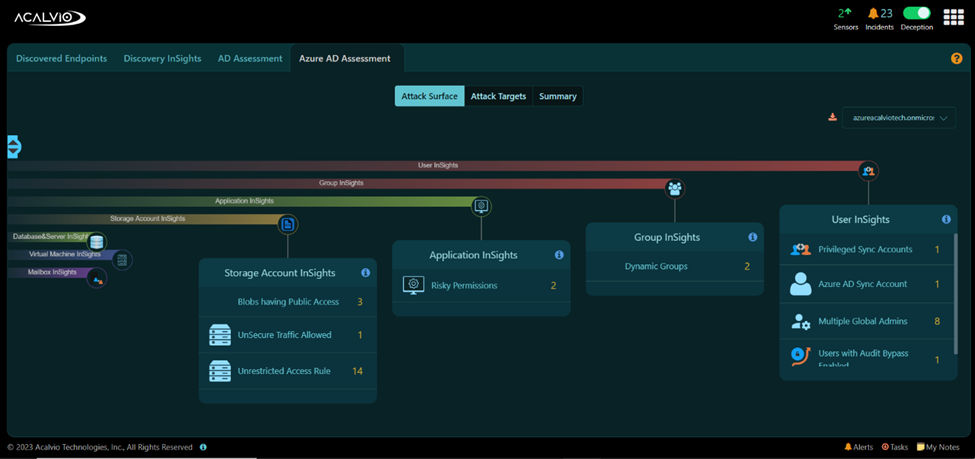
Acalvio ShadowPlex Identity Protection provides visibility into an organization’s identity attack surfaces and provides capabilities to detect and respond to identity based attacks.
Acalvio ShadowPlex features:
- Offers visibility into endpoint credential caches and generates insights into potential security weaknesses related to identities stored in Active Directory (AD), Azure AD, and Active Directory Certificate Services (AD CS).
- Provides attack path analytics that shows pathways that attackers can exploit to reach information assets.
- Identifies which credentials in repositories and on endpoints belong to privileged users such as top executives and system administrators.
- Discovers credential caches on key assets across the enterprise, including servers, workstations, and laptops.
- Supplies deception tools to identify and stop identity-based attacks. Security and identity management teams can detect malicious activities while attackers waste time trying to exploit decoy credentials.
Conclusion
Acalvio ShadowPlex Identity Protection defeats identity-based attacks with identity attack surface management and active defense. This comprehensive ITDR solution integrates seamlessly with the security ecosystem to secure enterprise identity assets.
Read more about Acalvio’s Identity Threat Detection and Response capabilities. Watch a short video overview. To find out how Acalvio ShadowPlex can protect critical identity assets in your organization, schedule a demo. Or contact Acalvio at info@acalvio.com.
FAQs on IDTR
How do identity threat detection and response solutions work?
Identity Threat Detection and Response solutions are aimed at securing the identities present in an enterprise network against identity based threats. They assess the potential attack surface and uncover identity related vulnerabilities. ITDR solutions also detect identity based attacks and alert security teams. They also integrate with SIEM and SOAR systems to respond to identity attacks by quarantining or isolating the affected systems.
How can organizations detect and respond to identity threats?
Organizations need to plan their identity security strategy. There are several preemptive measures that organizations can take to secure identities and reduce the attack surface. Such as implementing multi factor authentication and assessing the number of accounts with privileges. Implementing a comprehensive identity threat detection and protection solution is the most effective measure.
What are the potential consequences of a successful identity threat attack?
From research conducted by the Identity Defined Security Alliance, 78% of those who experienced an identity-related breach reported a direct business impact, 42% said it caused a significant distraction from the organization’s core business, 35% percent noted a negative impact on the organization’s reputation.
How can I stay informed about the latest threats and updates to identity threat detection and response?
Blog posts and websites that cover cybersecurity threats and security solutions provide coverage and analysis of attacks and techniques. Patches and security updates to software installed on enterprise networks help fix existing vulnerabilities. Comprehensive ITDR solutions incorporate the latest innovations in combating identity threats.