
The Flaws in Cybersecurity: Overlooking the Nature of Asymmetric Warfare
A critical aspect that is often overlooked is the nature of asymmetric warfare between the attackers and the defense teams. Any glitch in cyber security defense theories/practices is a winning amplifiable opportunity for the attackers, while there is no extra penalty or risk associated with attacker side missteps/errors. Attackers can continue “trial and error” until succeeding. This cyber security asymmetric warfare is due to the fact that the Internet was originally built on the top of a “trusted” model in which all the participants were considered to be collaborative with good intent, and all the digital assets, whether owned by individuals, enterprises, or governments, should be genuine and real. Attackers exploit the “trusted” model to the extreme.
What is Deception Technology?
Deception Technology is an advanced form of cyber defense, where deceptions that mimic real network assets are overlaid across the enterprise network and are used to lure and detect attackers. Since legitimate users have no reason to interact with a deception, any interaction with a deception generates a high-fidelity alert.
The Importance of Deception Technology
The number and types of cyberattacks have increased exponentially over the years and now even involve nation-states. Attackers can use easily available tools to exploit and attack all parts of an enterprise network.
Some figures from the CrowdStrike 2023 Threat Hunting Report include:
- 583% increase in Kerberoasting
- 312% increase in the abuse of remote monitoring and management tools
- 160% increase in credential theft
Traditional security layers are passive and only look for attacker behavior, activity, IoCs (Indicators of Compromise), or side effects. These are not enough to stop sophisticated cyberattacks.
Active cyber defense that leverages dynamic deception technology and predictive analytics is the new cybersecurity layer that can help defenders take back the advantage.
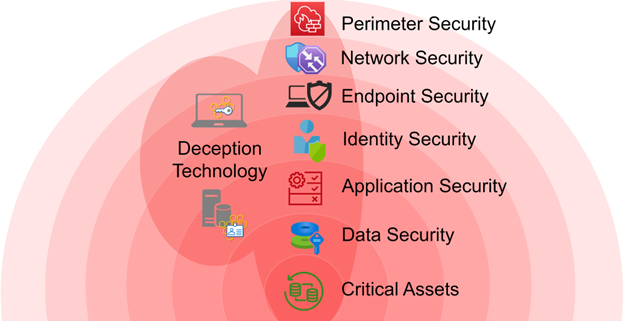
With a deception technology solution deployed, the attacker has to just interact with any one of these deceptive artifacts to get detected. Even if the attacker is aware that there are deceptions deployed on the network, they can’t do much to evade authentic-looking deceptions. Now the tables are turned, and the attacker will be detected sooner or later and contained quickly. Cutting edge solutions like Acalvio ShadowPlex leverage deception technology and AI to help organizations take back the defender’s advantage.
Benefits of Deception Technology
Enhanced Threat Detection
Since deception technology does not depend on attack signatures or other static indicators, it can detect a range of threats. For threats such as Ransomware that is the most prevalent attack today and evolves rapidly, cyber deception provides an extremely timely response to detect, arrest and deny access, with minimal or no manual intervention.
Significant Reduction in False Positives
Deception technology employs deceptive assets which are not real network assets or resources. If someone engages with a deceptive asset, it can’t be for legitimate business purposes and is therefore likely an intruder. Using deception techniques gives high-fidelity detections and defense teams are not spending time working through false positives.
Coordinated Defense Response
Advanced cyber deception technology solutions like ShadowPlex integrate with a wide range of solutions such as SOAR, SIEM, EDR, AD, and Network Management Solutions, among others. They leverage integrations with these defense systems for network discovery, gathering forensic data from endpoints, breadcrumb and bait deployment on network endpoints and assets, as well as for automated response.
Threat Intelligence
Solutions that employ deception techniques to detect attacks also gather intelligence about attack TTPs (Tactics, Techniques, and Procedures) based on actual observed behavior, which can be used for forensics or threat hunting.
Easy Scalability
With deception technology, the number of decoys and their distribution across the enterprise can be easily scaled. Fluid Deception and the sharing of compute resources allows organizations to minimize the amount of compute, storage, and software licenses required.
Conclusion
In cybersecurity, over the years, the relationship between the role of the attacker and the role of the defender has become highly asymmetric. Defenders must defend against all possible entry points that can be breached. They must learn to deal with living off-the-land tools and techniques. And the ever-growing list of easily available penetration testing tools. While the attacker has to exploit just one vulnerability or steal one VPN credential to get through these layers of security. This asymmetry highly favors the attacker.
With deception technology solutions like Acalvio ShadowPlex, anything can become a deceptive artifact. Using ShadowPlex, defenders can now embed deceptions everywhere, surround key assets with deceptions, intercept attackers in real-time, and proactively reduce the attack surface attack paths.
Frequently Asked Questions:
What is deception technology and how does it enhance cybersecurity?
What are the benefits of using deception technology in the fight against cyber-attacks?
Deception Technology based cybersecurity solutions offer the following benefits:
- Enhanced Threat Detection
- Significant Reduction in False Positives
- Coordinated Defense Response
- Threat Intelligence
- Easy Scalability
How does next-generation deception technology differ from traditional honeypots?
Next generation deception differs from traditional honeypots in many aspects by addressing the following complex problems:
– Deception sensors will not disclose themselves and are hard to be detected/fingerprint by the dark side;
– The combination of low – and high-interaction deception sensors/servers will enable scalable deployment in terms of volume, variety, and capability;
– Seamless integration with the existing/future perimeter-based security products/solutions will support better threat info gathering, processing, and response.


