- Products
-
ProductsPlatform
- ShadowPlex Advanced Threat Defense
Deception for early detection of cyber threats with precision and speed
- ShadowPlex Cloud Security
Multi-cloud Security Built on Enterprise-scale honeytokens
- ShadowPlex Identity Protection
Visibility of identity attack surface and comprehensive detection of identity threats
- ShadowPlex Threat Intel
Targeted Threat Intel Providing Preemptive Cyber Security
- Acalvio Active Defense Platform
Comprehensive and Award-winning Distributed Deception Platform
- What is Active Defense?
Active defense detects and diverts attacks.
- Why do I need Acalvio Active Defense?
Active Defense deceives and disrupts attackers.
- ShadowPlex Advanced Threat Defense
-
- Solutions
-
Technology SolutionsIndustry Solutions
- Early Threat Detection
Detect cyber threats early in the attack lifecycle to prevent adversary breakout
- Identity Threat Detection & Response
Detect identity threats with precision and protect the identity architecture
- OT Security
Protect OT environments from cyber threats with an easy-to-deploy and non-intrusive solution
- Red Teaming
Strengthen defenses to detect red team activities
- Threat Hunting
Active threat hunting to confirm latent threats and gain visibility to attacker TTPs
- Ransomware
AI-driven deception to protect against known and zero-day ransomware variants
- Honeytokens for CrowdStrike
Enterprise-scale honeytokens to protect against current and evolving identity threats
- Cloud Detection and Response (CDR)
Agent-less threat detection across multi-cloud environments using AI-Powered honeytokens
- Active Directory Protection
Visibility to AD attack surface and detection of AD attacks
- Zero Trust
Advance Zero Trust maturity through improved cyber visibility
- Insider Threats
Unmask hidden dangers. Cyber deception for high-fidelity insider threat detection
- Public Sector
Targeted solution for protecting Federal agencies in conformation with NIST and CISA recommendations
- Financial Services
Transform Financial Cybersecurity with Innovative Cyber Deception and Active Defense
- Healthcare
Active defense solutions thwart healthcare attacks before they can inflict real damage.
- Early Threat Detection
-
- Resources
- Partners
- Company
Red Teaming
What is Red Teaming?
A red teaming exercise is a proactive cybersecurity practice where a group of skilled and independent security experts, known as the “red team,” simulate real-world cyberattacks on an organization’s systems, networks, and physical infrastructure. The purpose of red teaming is to identify vulnerabilities, weaknesses, and gaps in an organization’s security defenses that might not be easily detectable through traditional assessments.
The red team employs various tactics, techniques, and procedures (TTPs) to mimic the tactics of actual adversaries, helping organizations better understand their risk exposure and improve their overall cybersecurity posture. The insights gained from a red teaming exercise can aid in enhancing incident response plans, strengthening defenses, and refining security strategies.
What Are the Objectives of a Red Team?
The primary objective of a red teaming exercise is to evaluate the security parameters of an organization by carrying out realistic attacks.
- Identify Weaknesses in systems, networks, applications, and processes that could be exploited by malicious actors.
- Test the effectiveness of security monitoring, incident response processes, and detection mechanisms.
- Provide recommendations to strengthen security controls and close identified gaps.
- Test the response of defensive security teams.
- Simulate attacks used by real-world adversaries, including advanced persistent threats (APTs) or insider threats.
By uncovering vulnerabilities and inefficiencies in a realistic but controlled manner, red teaming helps organizations proactively address risks and build a more robust security framework.
How Does Red Teaming Function?
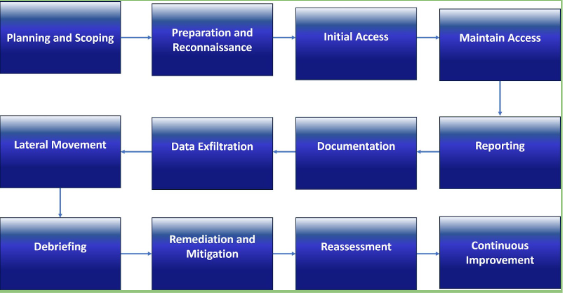
Red teaming is a structured and systematic approach to evaluating the security and effectiveness of an organization’s systems, processes, and defenses. The following are the steps involved in a red teaming process:
-
Planning and Scoping:
- Define objectives and goals.
- Determine the scope and boundaries of the exercise.
- Set rules of engagement for the red team.
-
Preparation and Reconnaissance:
- Gather information about the target organization.
- Analyze threat intelligence for realistic attack scenarios.
- Develop a detailed attack plan.
-
Initial Access:
- Attempt to gain initial access to the organization’s systems.
-
Maintaining Access:
- Establish persistence within the network.
- Create backdoors or exploit vulnerabilities.
-
Lateral Movement:
- Move laterally through the network to access other systems.
-
Data Exfiltration:
- Attempt to steal sensitive data or demonstrate the impact of a successful breach.
-
Documentation:
- Thoroughly document all actions taken during the exercise.
-
Reporting:
- Prepare a detailed report with findings, vulnerabilities, and recommendations.
-
Debriefing:
- Discuss results and lessons learned with stakeholders.
-
Remediation and Mitigation:
- Address identified vulnerabilities and weaknesses.
-
Reassessment:
- Periodically repeat the exercise to test improvements.
-
Continuous Improvement:
- Use insights to enhance security measures continuously.
- Red teaming helps organizations identify and mitigate security risks by simulating real-world attacks and evaluating their defenses and response capabilities.
Tools and Tactics of the Red Team
A red team uses the same tools, tactics, techniques that real-world cyber attackers do.
Tools:
- Reconnaissance Tools
- Exploitation Frameworks
- Phishing and Social Engineering Tools
- Credential and Password Attack Tools
- Post-Exploitation Tools
Tactics:
- Reconnaissance
- Initial Access
- Privilege Escalation
- Lateral Movement
- Data Exfiltration
- Persistence
- Evasion
What Are the Benefits of Red Teaming?
Red teaming offers several key benefits to organizations seeking to enhance their cybersecurity posture:
- By simulating real-world cyberattacks, red teaming uncovers vulnerabilities and blind spots that might otherwise go undetected, providing a comprehensive assessment of an organization’s defenses.
- This proactive approach helps organizations identify and address weaknesses before malicious actors can exploit them.
- Red teaming also fosters a better understanding of potential attack vectors, helping security teams develop effective strategies for incident response and mitigation.
- Additionally, red teaming enhances collaboration and communication among cross-functional teams, improves incident detection and response capabilities, and contributes to ongoing improvements in overall security readiness.
What are the differences between Red Teaming and Penetration Testing?
Red teaming and penetration testing are both crucial cybersecurity assessments, but they differ in scope and objectives. Penetration testing, often referred to as “pen testing,” focuses on identifying vulnerabilities in specific systems or applications to assess their security posture. Pen testers aim to exploit weaknesses and provide a detailed report of vulnerabilities discovered.
In contrast, red teaming is a broader and more comprehensive exercise that simulates real-world cyberattacks. The red team attempts to emulate the tactics of adversaries across various attack vectors, including social engineering, physical security, and more. The goal of red teaming is to assess an organization’s overall resilience and readiness by identifying potential blind spots and uncovering vulnerabilities that might be missed in traditional assessments. While penetration testing dives deep into specific targets, red teaming takes a holistic approach to test an organization’s entire security ecosystem.
What is the difference between the Red Team, Blue Team, and Purple Team?
The Red Team, Blue Team, and Purple Team have different roles during attack simulations.
The Red Team’s role is to simulate cyberattacks attacks and to test the company’s security systems. They act as the adversary in the exercise. They attempt to exploit vulnerabilities in systems, networks, and applications.
The Blue Team’s role is defensive security. They monitor, detect, and respond to threats. They try to detect, prevent, and mitigate the Red Team’s attacks.
The Purple Team’s role is to facilitate collaboration between the Red and Blue Teams. They share insights to improve overall security, developing actionable insights from Red Team findings for Blue Team improvements.
How can cyber deception help in Red Teaming?
Cyber deception plays a valuable role in red teaming exercises by adding a layer of realism and complexity to the assessment. By deploying deceptive elements like decoys, lures, baits, breadcrumbs, and false information, cyber deception provides the red team with dynamic scenarios that mimic actual attack situations. This challenges the red team to adapt their tactics and techniques, closely simulating the unpredictable nature of real-world adversaries.
The inclusion of cyber deception in red teaming enhances the exercise’s effectiveness by testing not only an organization’s technical defenses but also the ability of its security teams to detect, respond, and adapt to evolving threats in a dynamic environment.
FAQs
What is a red team in cyber security?
Can you provide an example of red teaming in practice?
Another common scenario is a red team that actively attempts to break into a company’s servers, Active Directory or other systems and datastores, gathering valuable insights into existing vulnerabilities.
What are the drawbacks of red teaming?
- Red teaming exercises require significant time, specialized skills, and financial resources to plan, execute, and analyze.
- Unlike continuous security measures, red teaming provides a snapshot of vulnerabilities at a specific point in time.
- Aggressive testing can disrupt business operations.
- If the organization doesn’t act on the red team’s recommendations, the exercise has little value.