- Products
-
ProductsPlatform
- ShadowPlex Advanced Threat Defense
Deception for early detection of cyber threats with precision and speed
- ShadowPlex Identity Protection
Visibility, management and protection of identity stores and attack paths
- Acalvio Active Defense Platform
Comprehensive and Award-winning Distributed Deception Platform
- What is Active Defense?
Active defense detects and diverts attacks.
- Why do I need Acalvio Active Defense?
Active Defense deceives and disrupts attackers.
- ShadowPlex Advanced Threat Defense
-
- Solutions
-
Technology SolutionsIndustry Solutions
- Breach Detection
Active Defense for breach detection and response, both in on-premises and cloud workloads
- Identity Threat Detection & Response
Visibility into Identity attack surface and effective detect & respond solution for identity attacks
- OT / ICS Security
Passive and low-risk agentless solution that is easy to deploy
- Active Directory Protection
Visibility into AD attack surfaces and detection of AD Attacks
- Threat Hunting
Active threat hunting, based on targeted deception, to confirm hunting hypothesis
- Ransomware
AI-Driven Advanced Deception Technology to combat even zero-day Ransomware
- Honeytokens for CrowdStrike
Honeytokens are deceptive credentials and data that are embedded in legitimate assets
- Zero Trust
Zero trust is a security model that assumes that no one inside or outside of the network can be trusted
- Public Sector
Targeted solution for protecting Federal agencies in conformation with NIST and CISA recommendations
- Healthcare
Active defense solutions thwart healthcare attacks before they can inflict real damage.
- Breach Detection
-
- Resources
- Partners
- Company
Zero-Trust Architecture
What Is Zero Trust Architecture? How Does Zero Trust Architecture Work to Secure an Organization’s Network?
Zero Trust Architecture (also known as Zero Trust Network Architecture or ZTNA)is a cybersecurity approach that challenges the traditional perimeter-based security model. It advocates for the principle of “never trust, always verify.” In a Zero Trust Architecture, no user or device, whether inside or outside the network, is automatically trusted. Instead, all entities must continuously authenticate and validate their identity and security posture before being granted access to resources.
This strategy reduces the attack surface, minimizes lateral movement by attackers, and focuses on strict access controls, encryption, micro-segmentation, and continuous monitoring to enhance overall cybersecurity and mitigate potential breaches. Figure 1 shows components that are secured by the Zero Trust architecture.
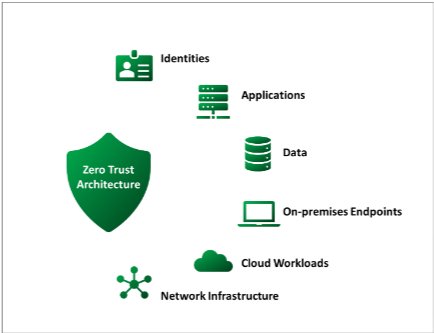
What Are the Benefits of Zero Trust Architecture?
Zero Trust architecture offers a range of benefits:
- Minimized attack surface by verifying users and devices
- Heightened security through strict access controls
- Reduced lateral movement of threats within a network
- Safeguards data through encryption and adaptive security, which effectively minimizes insider threats, and ensures the security of remote and cloud environments.
By aligning with regulations and limiting breach impact, Zero Trust architecture enhances incident response with continuous monitoring and rapid detection, contributing to a resilient cybersecurity framework.
What Are the Various Layers That Can Implement Zero Trust Architecture?
Zero Trust architecture encompasses multiple layers to ensure robust security. It begins with strong identity and access management, requiring user authentication and verification. Device security checks devices for vulnerabilities, while network segmentation and micro-segmentation divide the network into isolated zones to prevent lateral movement of threats.
Application and data security enforce access controls and encryption to safeguard resources. Continuous monitoring and analytics track activities in real-time, while policy enforcement ensures consistent security measures. Automation, orchestration, and user behavior analytics enhance adaptability and threat detection, creating a comprehensive and dynamic Zero Trust framework.
How Does Acalvio Support a Zero Trust Architecture Implementation?
Acalvio’s Advanced Threat Defense solution can play a crucial role in enhancing Zero Trust architecture implementation by adding a new layer of defense, with an emphasis on identity protection. By deploying cleverly crafted deceptions and deploying them across the network, a new dynamic environment is created that confuses and misleads attackers.
This proactive approach aligns with Zero Trust’s principle of continuous verification, diverting attackers’ attention away from key assets, and providing valuable time for defense teams to detect and respond to threats. In addition, Advanced Threat Defense enhances visibility across the network, aiding in identifying unauthorized activities and potential breaches.