Resources
Advancing State of Art in Cloud Malware Detection
Detecting attackers with kubernetes driven deception in cloud-native applications
Deceiving Attackers in a Kubernetes World
Deceiving Attackers in a Kubernetes World
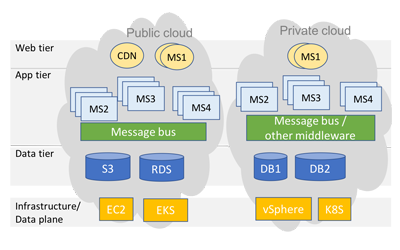
Unified Security in Hybrid Clouds: The Role of Kubernetes & Microservices
Enterprise workloads are rapidly migrating from on-prem data centers or private clouds towards public clouds, run by players such as Amazon and Microsoft. While CIOs and IT leaders have been spending the past few years reeling in these individual public cloud islands,...
Acalvio Research Shortlisted for Virus Bulletin Award
Virus Bulletin Shortlists Acalvio Research for Péter Szőr Award.
Dynamic Deception to address GDPR compliance
GDPR & Deception
Using Deception to Detect and Profile Hidden Threats
Author: Satnam Singh, Chief Data Scientist at Acalvio Technologies How do we detect and profile the adversaries who have already infiltrated and are hiding in the network? To answer this question, we need an approach that can improve the detection and provide more...
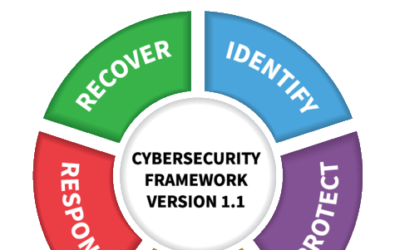
Rise Above the Fray with The NIST Cybersecurity Framework
Being a CISO these days isn’t easy. The threats are dynamic, the technology hype bewildering, and the expectations from the boss to magically “just make the problem go away” unrelenting. One way to help get a grip on this mess is to adopt industry accepted frameworks...
Lateral Movement Technique Employed by Hidden Cobra
US-Cert recently issued notification regarding malicious cyber activity by the North Korean government [1] Hidden Cobra.
Lateral Movement Technique by Hidden Cobra Threat Actor
US Cert recently issued notification regarding malicious cyber activity by the North Korean government [1] as Hidden Cobra. There are two families of malware used by the North Korean Government. Remote Access Tool (RAT) known as Jonap A Server Message Block (SMB)...
Using Deep Learning for Information Security – Part 1
Balamurali A R and Satnam Singh – Post Web 2.0, data generated on the internet has increased manifold. This has led to the use of data driven approaches to solve many traditional problems across different industry verticals.
Deception Deployment Strategies : Threat Agnostic vs. Service Agnostic
In our previous blogs[1][2], we have shared details of detection of breach campaigns and worms by using Deception. A Distributed Deception Platform (DDP) consists of the breadcrumbs and lures at the endpoint pointing to the honey services in the network. The DDP can...
Detection of Breach Campaigns by using Distributed Deception
Today’s breaches are predominantly carried out in a series of sophisticated, multi-stage attacks. The stages involved in such an attack can best be described by a “Cyber Kill Chain". This, as per MITRE ATT&CK Adversary Tactic Model [11] breaks down cyber...