Zero trust is a security model that assumes that no one inside or outside of the network can be trusted unless their identity and access is verified. It follows the principles of least-privilege access, continuous verification and assume breach.
Federal and commercial agencies are adopting Zero Trust to protect the critical assets and sensitive data from breaches. The DoD and CISA zero trust frameworks are two of the most comprehensive guides for zero trust.
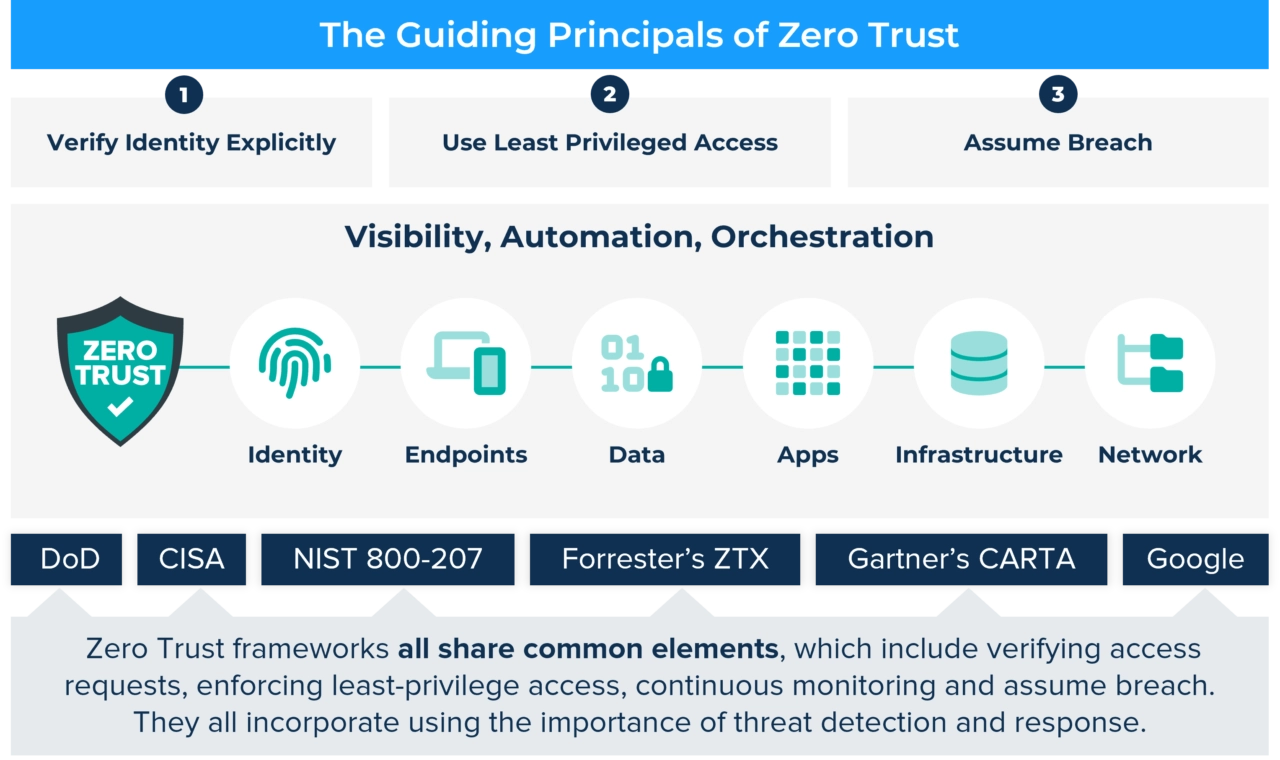
Zero Trust Models
The DOD framework has seven pillars and the CISO model has five pillars and provides a maturity model.
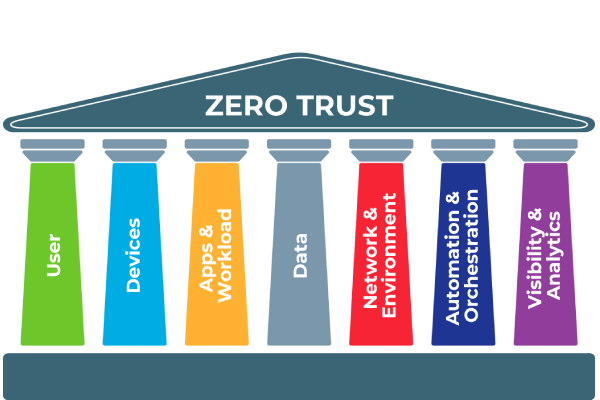
DoD: Zero Trust Pillars
The DoD zero trust pillars provide the foundational areas for the DoD Zero Trust Security Model and the DoD Zero Trust Architecture.
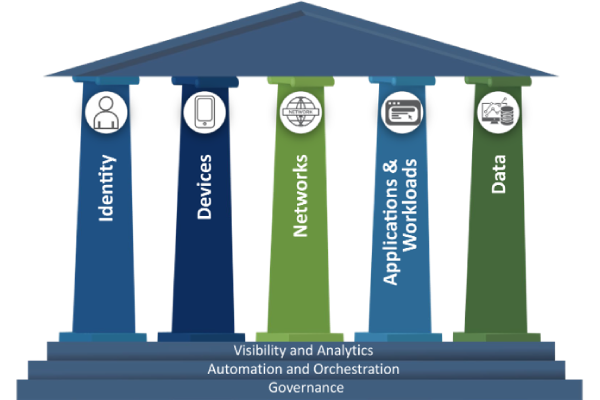
CISA: Zero Trust Maturity Model
Each pillar includes general details regarding the following cross-cutting capabilities: visibility and analytics, automation and orchestration, and governance.
Cyber Deception in Zero Trust
No Zero Trust model is complete without visibility and analytics. Cyber deception advances Zero Trust maturity by providing proactive threat detection, expanding detection coverage and enhancing overall security.

Proactive Threat
Detection
Threat detection that is
agnostic to attacker
TTPs. Detect zero days

Early Threat
Detection
Detect threats before
adversary breakout time

Protect Critical
Assets
Prevent attack
propagation through
strategically placed
deceptions
Strategic Technology Roadmap
for Deception Technology and Zero Trust
CISA published top recommendations in its 2022-2026 Strategic Technology Roadmap. The recommendation is to adopt Deception Technology strategies within the next two years.
Benefits of Cyber Deception in a Zero Trust Security Posture
Cyber deception improves a company’s zero trust security posture with techniques that uses decoys, traps, false credentials, and lures to mislead and confuse attackers, while detecting and responding to malicious activities.

Protect
Identity
Stores

Prevent
Adversary
Breakout

Protect
Sensitive
Data

Enhance
Threat
Detection

Increase
Attacker
Costs

Threat
Hunt
Key Use Cases for Zero Trust and Cyber Deception
EXPAND THREAT DETECTION
- Set traps based on the mission or objectives of the threat
- Does not require a prior knowledge of threats
ENHANCE SOC EFFICIENCY
- Adds high-fidelity attack detection to avoid alert deluge
- Automated response to prevent attack propagation
ACTIVE THREAT HUNTING
- Delivers an active approach to threat hunting
- Identifies latent threats
- Hypothesis testing and confirmation
DETECT IDENTITY (ITDR)
- Deploy AI-recommended deceptive identity artifacts
- Interaction generates alerts with precision and speed
- Independent of known offensive techniques
PROTECT UNMANAGED ENDPOINTS
- Deploy deceptions to detect threats originating from unmanaged endpoints
- Ideal for network and IoT/OT devices that cannot use EDR
IDENTIFY INSIDER THREATS
- Embedding deceptions deter individuals, detect activity, and disrupt efforts
- Fast investigations with clear proof of unauthorized access
To Learn More About Zero Trust
Next Steps
Explore our patented technologies to enable Active Defense and Identity Security in your enterprise.


