Resources
Defending against identity impersonation attacks at MGM Resorts
MGM Resorts was compromised by a threat actor, Scattered Spider (UNC3944). The threat actor gained control over the super administrator account of Okta, gained Azure administrative rights, and gained Domain Admin privileges over the Active Directory.
Deception: The Fast Track to Zero Trust Security
Zero Trust is a great idea that’s hard to argue with
Combating Log4Shell Exploits
Why Is a Log4Shell Exploit Considered a Serious Risk to Enterprises? Apache Log4j is used in thousands of enterprise applications across the stack and appliances with a web interface. Log4j is also an embedded component of many Java-based OT/ICS hardware and software...
Deception Tech in Healthcare: Addressing Device Risks – Acalvio
Healthcare institutions are heavily targeted by cyber attackers. The critical services these institutions provide, the volume of sensitive data they handle, the mix of IT and OT infrastructure, and unpreparedness make healthcare institutions very attractive and...
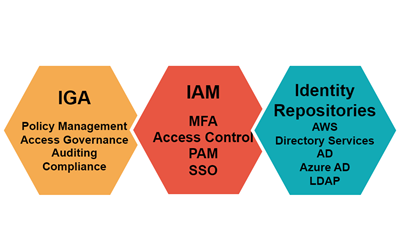
Identity Security Part 2: The Identity Security Ecosystem
This blog describes the identity security ecosystem. The blog covers the components of an identity security ecosystem, what each component does in an enterprise, and describes some limitations.
Identity-Based Attacks: A Breakdown of Types and Mechanisms
Cyberattacks have become a persistent threat to organizations across sectors. As the cyber threat landscape grows more complex, attacks are becoming larger and more scalable.
Acalvio & CrowdStrike Boost Identity Security with HoneyTokens
Acalvio Technologies and CrowdStrike Falcon® Identity Protection help customers combat increasingly sophisticated identity-based attacks.
Mitigating Microsoft Email Hack Attacks on US Federal Agencies and Western European Government Agencies
A Chinese hacking group breached email accounts of several US and Western European government agencies. What was their modus operandi and primary motive?
MOVEit Breach: The Active Defense Solution
Earlier this month, we witnessed the US Department of Energy, several other government agencies, banks and other commercial organizations hit in a global hacking campaign
Comprehensive Identity Protection through ITDR
Identity based attacks are rising dramatically. According to Verizon’s 2022 Data Breach Investigation Report, credential-based attacks have become the top path for threat actors to reach enterprise information assets.
MITRE ATT&CK Use Cases for Cybersecurity
As discussed in this whitepaper, the MITRE ATT&CK framework is a critical technology resource that can help you systematically evaluate your security measures against the potential threats you may encounter. Understanding the weaknesses in your current cybersecurity...
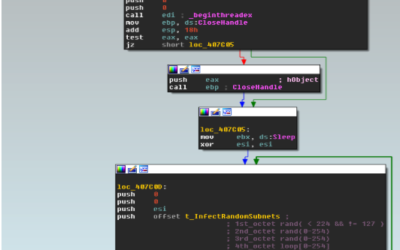
WannaCry Ransomware Analysis: Lateral Movement Propagation
In May 2017, the WannaCry ransomware attack made front-page news around the world, with at least 150 countries and over 200,000 customers affected by the attack. The WannaCry ransomware made use of an exploit that targeted the SMB protocol of Microsoft Windows.