Resources
A Game Between Adversary and Defender
The motivation for this blog is a question that has been circling in my head for a long time, and I have asked this question to many security analysts: Have they played a game with an adversary? or in other words - Have they engaged with an adversary? I got mixed...
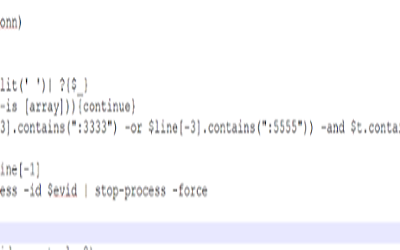
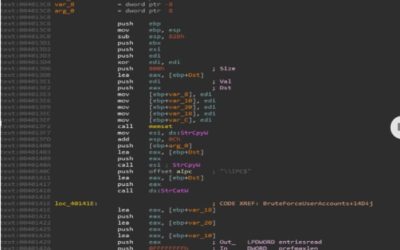
WannMine – Lateral Movement Techniques
Acalvio Threat Research Labs Introduction: Cryptominer is quickly becoming one of the greatest threats that is facing our industry. Similar to ransomware, it provides an easy avenue for a threat actor to monetize his/her skills. In one of the earlier blogs, we...
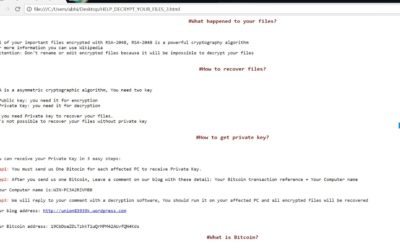
Technical Analysis of Samsam Ransomware.
Ransomware continues to represent the most critical threat facing organizations in 2018. In the latest breaches at Hancock Memorial Hospital, Adams Memorial Hospital, and Allscripts, SamSam ransomware was used to encrypt the files. In this blog, we dive into the...
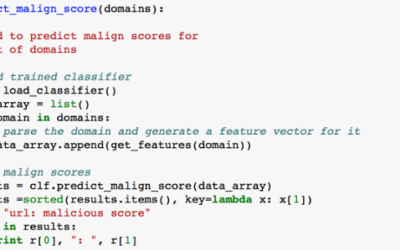
Ransomware Command and Control Detection using Machine Learning
Authors: Deepak Gujraniya, Mohammad Waseem, Balamurali AR, and Satnam Singh Since the first attack in 1989 [1], ransomware attacks have gained popularity. Especially in 2017, it has created havoc in every possible industry, including the government offices,...
Zealot Campaign Analysis & Detection via Deception Architecture
Acalvio Threat Research Labs Web Servers are becoming one of the entry vectors in breaches. In the last blog, I had shared the details of deception based architecture to prevent breaches involving web server as an entry vector. In this blog, we take Zealot campaign...
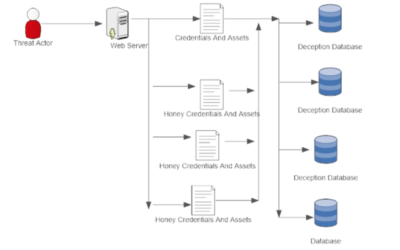
Deception-Based Architecture to Guard WebServer – Acalvio
Web Server is becoming one of the critical vector which have been exploited by a threat actor to breach an organization. Breach at Equifax is one such example, affecting 143 million customers. In this breach, a threat actor could access the internal network and...
Beyond the Hype: AI in Information Security
In the next few years, Artificial Intelligence (AI) will transform and expand as a decision engine across every enterprise business layer from product development to operations to finance to sales. While, internet biggies like Google, Facebook, Microsoft and Saleforce...
Lateral Movement of Emotet
Acalvio Threat Research Labs. Introduction Emotet is one of many information stealer malware families which have been active in the recent months. The initial delivery vector of the malware is via phishing campaign. The blog by TrendMicro[1] and Microsoft[2] discusses...
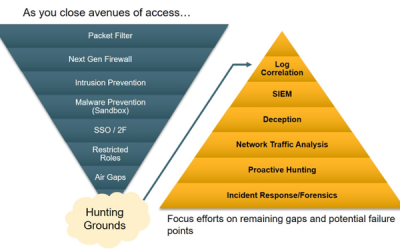
Three Minutes Until the Apocalypse
This blog covers three main topics: Three Key Questions Needing Answers Within Three Minutes When You Suspect a Breach Using Deception and Endpoint Logs to Backtrack Command and Control Improving SOC Triage Workflow with Prevention Failure Detection An adversary has...
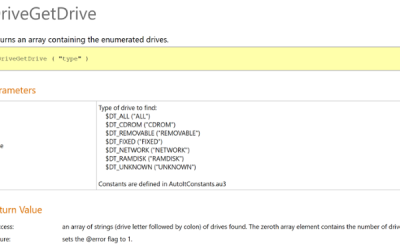
Spreading Technique used by Retadup Worm.
Acalvio Threat Research Lab Retadup worm has been in the news recently. It was first observered infecting Israeli Hospitals [1] and recently it was observered active in South America mining for Crypto Currency[2]. The details of the worm have been published by Trend...
Deception Centric Defense Against Ransomware
Team Acalvio It is estimated that in 2017, damages due to the ransomware will exceed $5 billion.[8] When successful, ransomware can not only infect the endpoint, it can also spread across the network extending its exploit. The initial versions of ransomware like...
HIPAA Compliance via Acalvio’s ShadowPlex Deception 2.0
The recent ransomware attacks such as Wannacry have highlighted the need for robust security controls in healthcare firms. These organizations are subject to HIPAA/HITECH compliance requirements, but unfortunately many firms just seem them as a distraction. This is...